Last week brought with it some malicious comebacks. The notorious Clop ransomware made a reappearance just a few days after the arrest of six gang members. Additionally, after a hiatus of nearly two months, the hacking group Molerats has attacked Middle Eastern government agencies.
Let’s dive into the details.
What’s Clop Ransomware up to?
What is Molerats? Molerats is an Arabic-speaking, politically motivated threat group operational. It has been in operations since 2012. The APT has specifically targeted government institutions across several countries including the U.S., the U.K, Israel, Palestine, China, India, and more. It uses spear-phishing techniques in all of its attacks with politically themed content. |
Early last week, the Ukrainian police, accompanied by the officials from South Korea and the U.S., carried out a law enforcement operation. Assisted by the security team from Binance – a cryptocurrency exchange, the team arrested six suspects linked to the Clop ransomware. As per Binance, the group, also known as FANCYCAT, was involved in cyber-attacks as well as money laundering activities.[1]
It is estimated that FANCYCAT laundered approximately $500 million worth of cryptocurrency collected as ransom for attacks carried out with Clop and other criminal groups. In the operation video released by Ukrainian police, the officials can be seen seizing 500 million Ukrainian hryvnias (approx. $180K), computer equipment, high-end cars like Mercedes and Tesla, and several documents.
As per the Ukrainian police, they were able to shut down the server infrastructure being used by the gang as well.
Recent attacks by Clop Ransomware
The Clop operation, however, had a limited impact on the ransomware gang’s operations as it attacked two new victims only a few days later. As per TechCrunch, the gang released a fresh batch of confidential data stolen from a farm equipment company and an architect’s office.[2]
The incident hints toward a minor impact of the recent arrests on the group. It could be a possibility that those arrested belonged to a lower rung in the gang.
"The law enforcement raids in Ukraine associated with CLOP ransomware were limited to the cash-out/money laundering side of CLOP's business only," @Intel471Inc https://t.co/bPOCY4Xc31
— Intel 471 (@Intel471Inc) June 16, 2021
However, it is to be seen how long the group can stay operational. With Russia committing to co-operation with the U.S. authorities and the recent recovery of ransomware paid by Colonel Pipeline, it might as well be a possibility that the ransomware group might be abandoned like Darkside.
How to prevent a Clop Ransomware attack?
- Be cautious about email attachments or links. Do not open/download any file or click any link if the email or files look suspicious.
- Do not download applications from any third-party sources as they tend to be spammy and malicious.
- Keep your system and apps updated with the latest software updates. Ensure that the updates are released by the official developer only.
- Deploy advanced detection and resolution capabilities with Netenrich Attack Surface Intelligence and Intelligent SOC.
Molerats resurfaces with new attacks on government networks in the Middle East
What is Clop Ransomware?
First discovered in Feb 2019, Clop ransomware is a variant of CryptoMix and shares similar TTP’s with Ryuk and BitPaymer. The ransomware uses executables that are code-signed with digital signatures to trick the security software to let it pass. The group is linked to some of the most high-profile attacks against industries such as Aerospace and Defense, Pharmaceuticals, Healthcare, Manufacturing, and more. |
Riding on the ongoing wave of violence between Israel and Palestine, Molerats (aka Gaza cybergang, and TA402 APT group) targeted government entities across the Middle East and worldwide with an interest in the region. The attacks came in a few weeks after the alleged ceasefire agreement between Hamas and Israel.[3]
The threat actor launched a series of spear-phishing attacks by sending malware laced PDF. The email claimed to have details on a meeting between Hamas and the Syrian government and a list of details on Hamas members. Once installed on the host computer, the malware gives the attackers access to all the files and allows it to take screenshots for spying purposes. Leveraging geo-fencing URLs, Molerats followed the following model of attack:
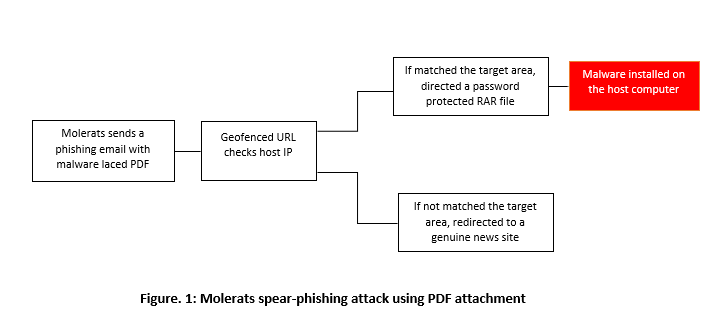
Most of the institutions targeted belong to government administration, telecommunications, finance, military, education, and technology.
Security recommendations:
- Increase awareness about phishing and spear-phishing campaigns within your organization across departments. Run regular tests and training programs.
- Create a back up of your important data and files in the 3-2-1 format i.e., create three copies of a file in two different formats and store the backups in a different location.
- Keep your systems, applications, and programs updated as per the official upgrades.
KNOW your attackers
Netenrich’s KNOW threat Intelligence dashboard continues to capture all this and more on known and unknown threats. Get your account today to access the updated threat intelligence for a better security posture.
Claim your free account
Related readings:
- Clop Ransomware – How a Bombardier Suffered a Data Breach
- Molerats Espionage In Middle East: KNOW Your Emerging Threats
Subscribe To Our Newsletter!
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.
Thank you for subscribing!




