REvil ransomware, a Russian hacking group also known by the name Sodinokibi has targeted Apple Inc. in a $50 million ransomware attack. This attack was followed by the theft of engineering and manufacturing schematics of current and future products from Quanta – A Taiwanese company that manufactures for Apple Inc. The notorious group is hoping for Apple Inc. to pay by 1st May, and threatened to post new images of the current and future product schematics if their demands are not met.
Quanta confirmed the breach in a recent statement commenting: “Quanta computer’s information security team has worked with external IT experts in response to a cyberattack on a small number of Quanta servers.” The breach goes on to show that every enterprise in this world is prone to a cyber attack. Whether you are a small, mid or large enterprise, you can be sure that the attackers are sizing you up, and if not now, they are just waiting for the opportune time.
Why is REvil Ransomware Feared?
For detailed insights about REvil ransomware, check out our blog covering the topic – Trending Malware of the Week. Over the last month, REvil ransomware has been on a hacking rampage with staggering numbers – $25 million Pierre Fabre, $50 million Acer, $24 million AsteelFlash, and now Apple, the list goes on. Gangs like REvil ransomware target higher paying targets and demand a hefty sum and later negotiate the ransom payoffs. Here’s REvil ransomware modus operandi:
- The operator works with vetted affiliates
- Operator provides affiliates with crypto-locking malware and technical support
- Affiliates infect the victims’ systems with malware
- The operator gets a cut for every affected victim that pays
- Many operators maintain a data leak site for affiliates to post stolen data
REvil ransomware gang starts with naming and shaming the victims, and then follows it up with leaking the data. If the victim still doesn’t pay the finalized ransom, the stolen data is typically dumped for free to scare future victims. The sensitive data is also auctioned to interested parties for a hefty amount.
How To Protect Against REvil Ransomware?
Threat detection and response is one of the ways enterprises protect their network from a cyber attack. As threats evolve, enterprises need to further enhance their cybersecurity. Interesting to note that Apple Inc. spent a massive $18.75 billion on research and development in the financial year 2020. A company that spends so much on research, imagine their spending on cybersecurity. Well, if a large organization can be hit and affected with REvil ransomware, what should a small and medium enterprise do to protect against an attack?
Netenrich addresses this issue by providing the most sophisticated threat and attack surface intelligence solution for faster detection, insights, and response to serious threats before they turn out into a full-blown attack. Check how Knowledge Now (KNOW) can help enterprises. KNOW is a free global threat intelligence tool that provides information that helps analysts learn more about the malicious activity, gain technical context, and relevant details 15x faster compared to that of the traditional approach. With a consistent and compelling approach to cyber threat research and intelligence, CyberSec professionals can efficiently tackle the daily challenges rather than drowning in the sea of alert fatigue.
REvil Ransomware Insights From KNOW
Here’s how the overview section from KNOW looks like for REvil ransomware or Sodinokibi.
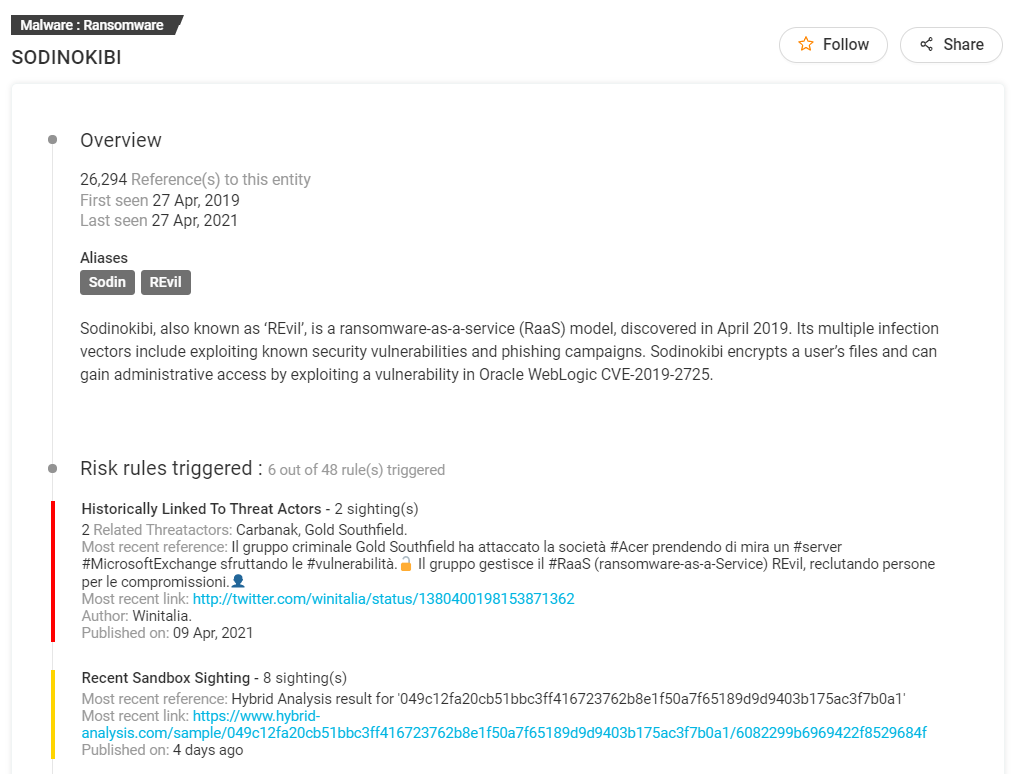
A complete overview in the first section helps you understand the risk rules triggered, aliases, sandbox sightings, references, historically linked threat research, C&C server, intrusion methods, and more. You can also benefit from the reference graph as shown below.
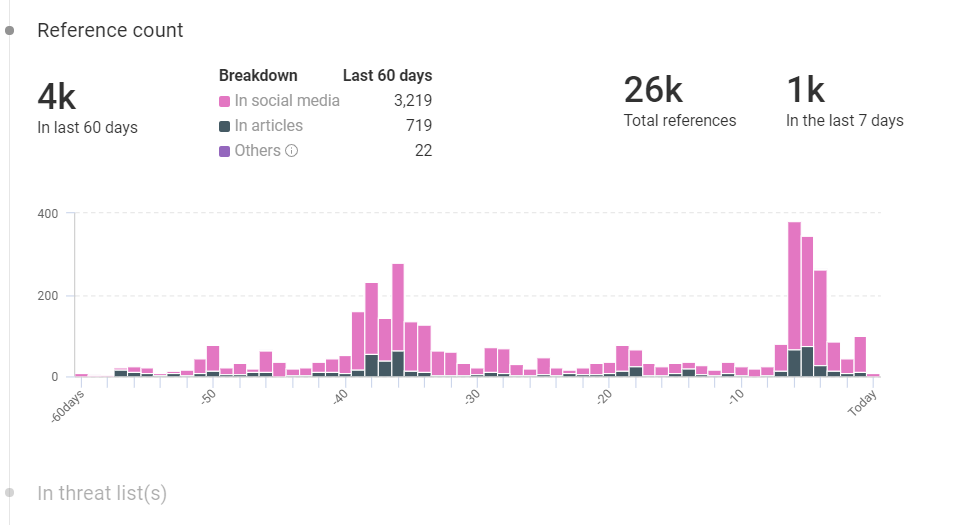
As a threat researcher or professional analyst who wants detailed insights into the most trending or past ransomware, you will have every relevant detail from across the globe compiled for you in an intelligible and easy to access format for FREE! Isn’t that outstanding? Well, there’s a lot more than threat intelligence offered by Netenrich. The objective to tackle every problem is to implement a solution, and with a resolution intelligence platform from Netenrich, enterprises can experience first hand the use of the most advanced technology in action with strategic thinking.
KNOW – Trending Threat Actors
According to KNOW, Carbanak was a trending threat actor recently. Carbanak or Anunak APT has many aliases such as Carbon spider, Anunak, FIN7, TAG-CR1, and Gold Niagra. This cybercrime group has successfully extracted millions from banking financial institutions from Russia, Ukraine, China, USA, and Germany. The group leveraged the SWIFT banking groups into their attack.
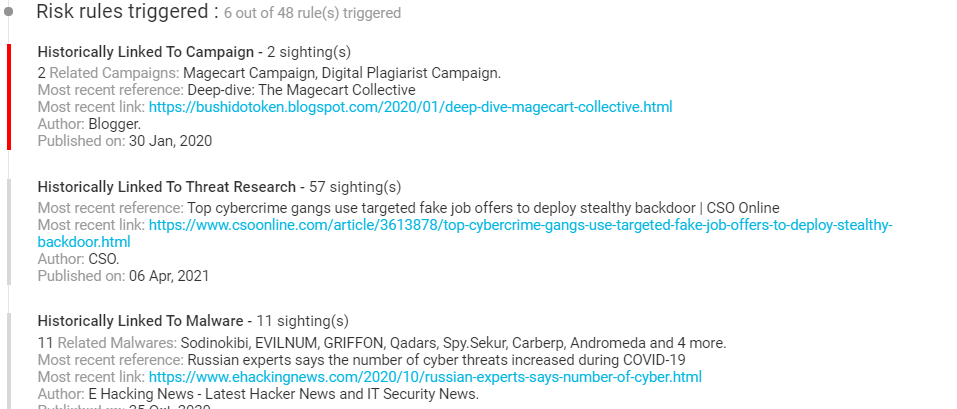
How Does Carbanak Threat Actor Attack?
The primary means of attacking a victim is by phishing mails. The victims are targeted through phishing mails with cpl attachment and the actor will continue to move around in the infected network until a system of interest is found. The group then installs Carberp backdoor with the capability of RDP, Keylogging, and video capture to get access to victims banking policy to strategically extract money. The group has also successfully infected and accessed many ATM servers which are accessed by the mules to extract money.
Trending Carbanak Tweets from KNOW
Carbanak and FIN7 Attack Techniques https://t.co/ctxXmgu4uC
— 01_security (@01_security_01) April 22, 2021
Possible FIN7 domain occasionent[.]com was registered on 4/8 and is hosted on a dedicated server at 94.103.81[.]160.
In @ThreatConnect: https://t.co/m73rlQdLHm pic.twitter.com/dBtMF6SVpA
— Kyle Ehmke (@kyleehmke) April 12, 2021
A member of the #FIN7 group was sentenced to 10 years in prisonhttps://t.co/9VkII9RPXZ#securityaffairs #hacking
— Pierluigi Paganini – Security Affairs (@securityaffairs) April 20, 2021
Carbanak Context From KNOW
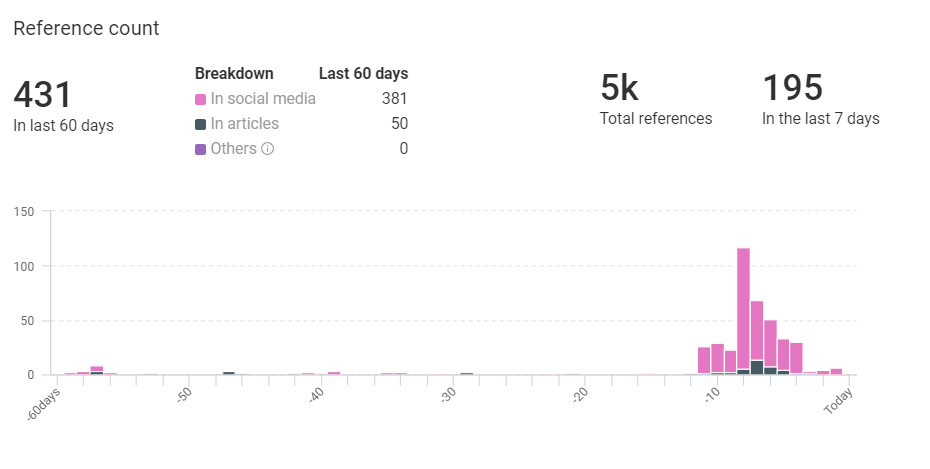
Threat Intelligence and Mitigation With Netenrich
KNOW gives you threat intelligence to work with, but how do you mitigate the risks? How equipped is your SOC (Security operations center) or IT team to handle advanced threats such as REvil ransomware and Carbanak? If you are a cybersecurity professional looking for consistent and comprehensive threat intelligence, KNOW is just right for you.
In this context, Frost & Sullivan has predicted that by 2022, the growing gap between qualified cybersecurity professionals and unfulfilled positions will be 1.8 million. Netenrich enables small and mid-sized enterprises to fill this huge gap with Resolution Intelligence to streamline threat detection, incident response, site reliability engineering, and achieve many such business goals.
If you’d like to continue receiving the most trending cybersecurity news and threat intel, sign up to KNOW. If you want to understand how Netenrich’s resolution intelligence can help you transform your IT operations and empower your existing teams and technology, get in touch with our resolution-oriented team.
Subscribe To Our Newsletter!
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.
Thank you for subscribing!




