Today let’s focus on the most trending attack methods of the week. As per KNOW’s threat intel dashboard, “Malware” is the most trending attack method of the last seven days with over 12,000 references.
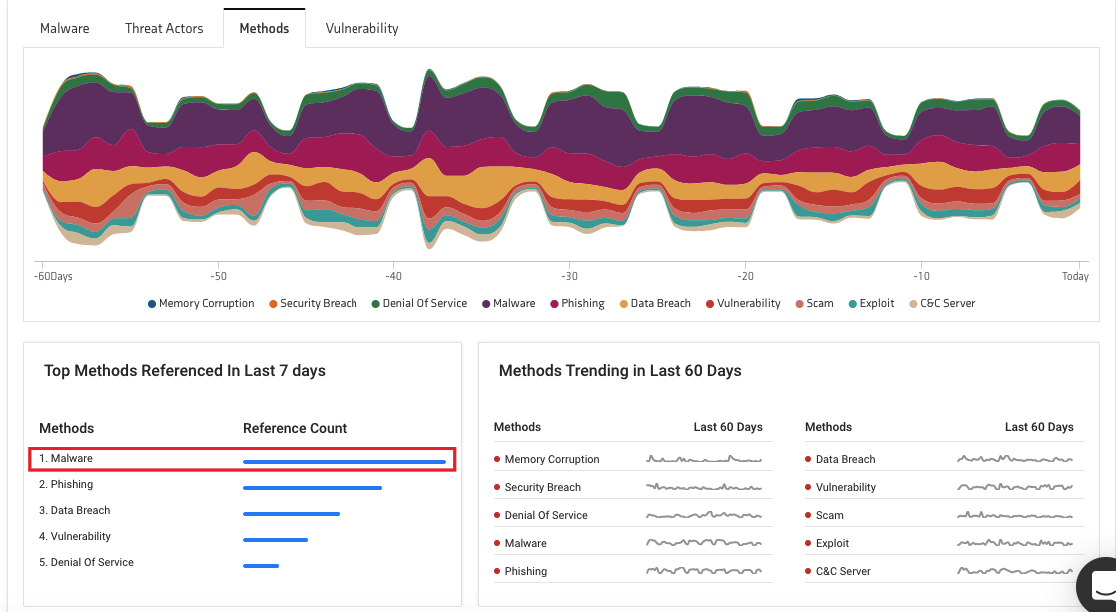
KNOW the most trending malware stories
As we have already mentioned before, KNOW is not just a threat intel dashboard, but it also happens to be a news aggregator serving up the latest and hottest stories in the cybersecurity space. KNOW also happens to collate these stories in different categories. Let’s check out the most trending news in the “malware” category.
The most trending story in the malware category happens to be about the ransomware attack on a German hospital that caused a woman’s death. As per reports, this attack has been linked to the infamous Russian ransomware gang – Evil Corp.
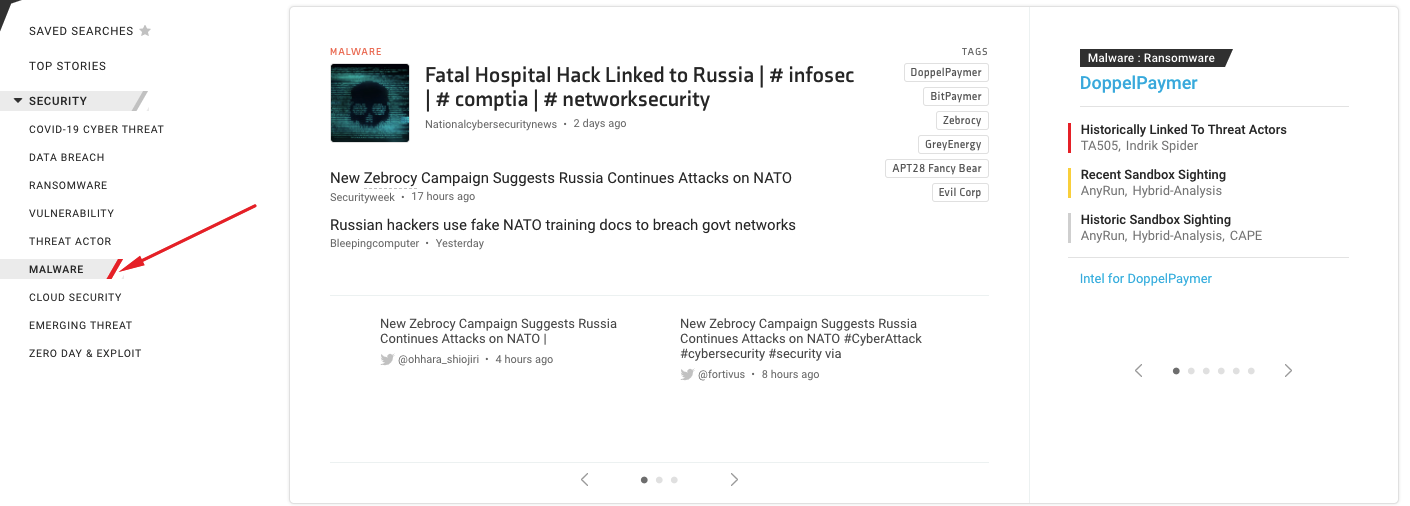
How did this malware attack happen?
Apparently, attackers exploited a vulnerability in some commercially available Citrix software to attack the Düsseldorf University Clinic (DUC). Patients who needed urgent care were diverted to another hospital 20 miles away. One of the patients, unfortunately, ended up losing her life.
Reactions from Twitter
In case you missed it… A patient dies after #ransomware attack paralyzes a German hospital systems—reportedly first casualty linked to a #cyberattack on a hospital.
A patient died when a German hospital was hit by ransomware, causing delays in life-saving treatment. Looks like the fears of healthcare cybersecurity professionals have come true 🙁
German police have confirmed this has been opened as a homicide investigation, against the ransomware folk.
Governments and industry need to put serious focus on ransomware groups and prevention. This is escalating – going to get worse
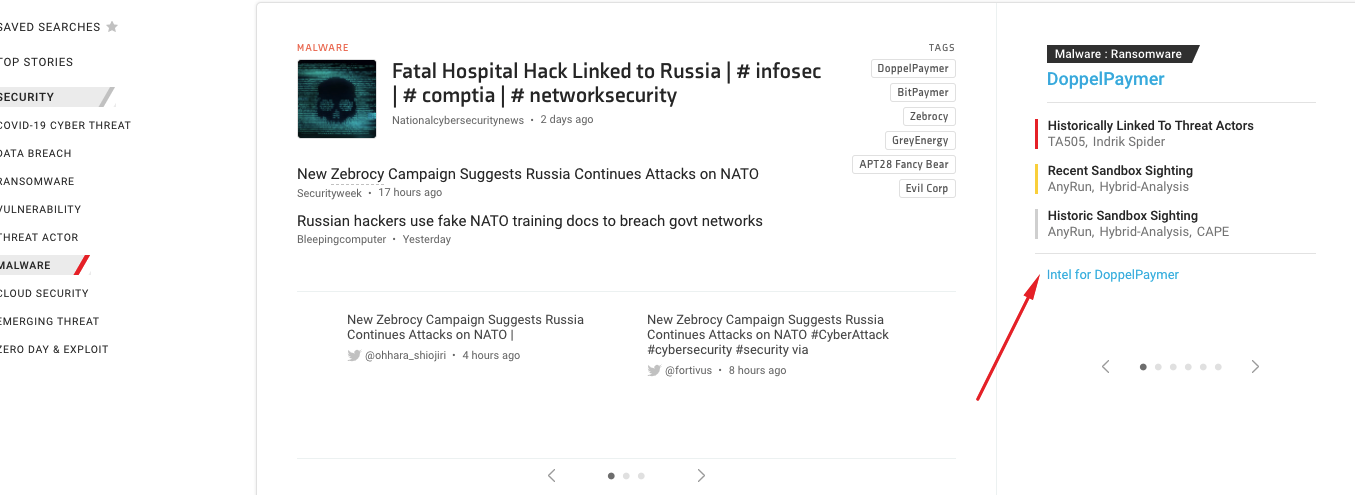
On the right-hand side of the screenshot above, you will see a story card with all the related malware and threat actors. Let’s check them out.
Malware detected by KNOW
#1 Doppelpaymer
- Risk rules triggered: 5 out of 48.
- Related intrusion methods: Double Extortion, Brute Force, Exfiltrate data, Data Exfiltration, Data exfiltrate, Brute Force Attack, Data Breach, etc.
- Most recent sandbox reference: Any Run Sandbox result for DoppelPaymer.RANSOM
- Related industries: Education, Healthcare, Aerospace, And Defense Manufacturing.
- Vulnerabilities: CVE-2019-1978 and CVE-2019-19781
- Related threat actors: TA50 and Indrik Spider.
References detected
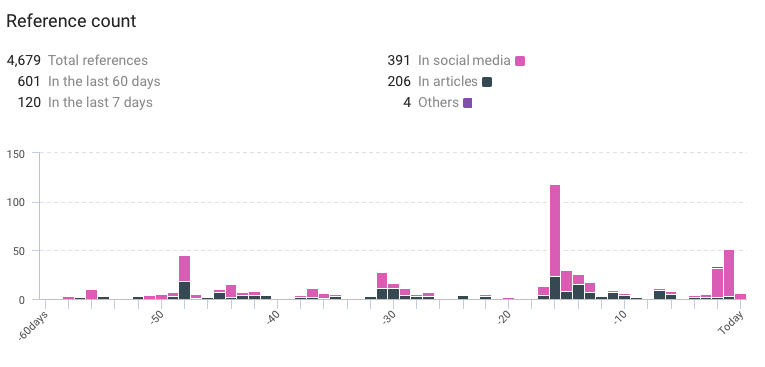
- Total references: 4,679.
- References in the last 60 days: 601.
- References in the last 7 days: 120.
#2 BitPaymer
- Risk rules triggered: 6 out of 48.
- Detected hashes: 19
- Related Intrusion Methods: Double Extortion, Privilege Escalation, Data Breach, BlueKeep, Phishing, Zero Day, Denial Of Service, etc.
- Most recent sandbox reference: Any Run Sandbox result for 8c54bb.exe
- Most recent C&C server reference: Empire C2 used by the #BitPaymer ransomware gang.
- Related industries: Hospitals.
- Related Threatactors: Evil Corp, Indrik Spider, and TA505.
- Delivers: Dridex.
References detected
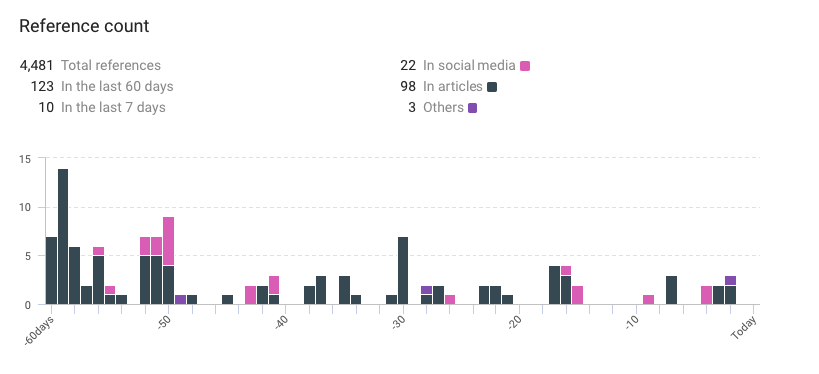
- Total references: 4,481.
- References in the last 60 days: 123.
- References in the last 7 days: 10.
#3 Zebrocy
- Risk rules triggered: 4 out of 48.
- Detected hashes: 33
- Related Intrusion Methods: Malware.
- Most recent sandbox reference: Hybrid Analysis result for ‘054c5aa73d6b6d293170785a82453446429c0efc742df75979b760682ac3026b’
- Related domains: 1 (http://backdoor.win32.zebrocy.gq/)
- Related Threatactors: APT28 Fancy Bear.
References detected
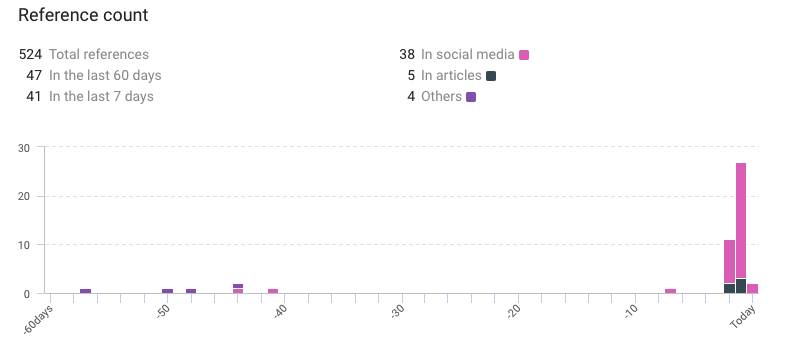
- Total references: 524
- References in the last 60 days: 47
- References in the last 7 days: 41.
#4 GreyEnergy
- Risk rules triggered: 4 out of 48.
- Detected hashes: 70
- Related Intrusion Methods: Fileless Attack Technique, Man-in-the-middle Attack, Phishing, and Spear Phishing.
- Most recent sandbox reference: Hybrid Analysis result for ‘f617e805ccd0b1451e1f448d1328201d79cb846ba8b5b97221c26188fd1a1836’
- Related Threatactors: Sandworm Team.
References detected
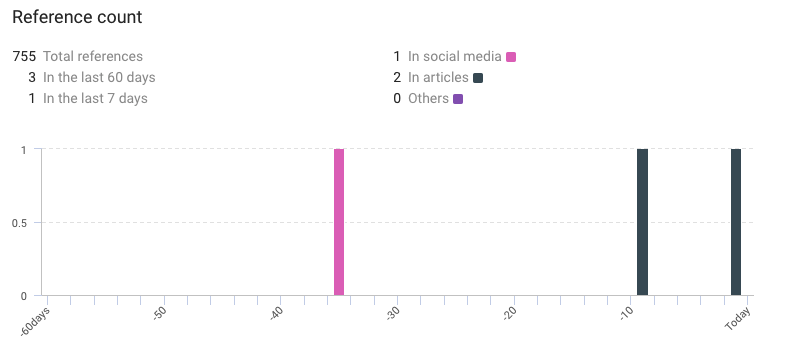
- Total references: 755
- References in the last 60 days: 3
- References in the last 7 days: 1.
Threat Actors detected by KNOW
#1 Evil Corp
- Risk rules triggered: 6 out of 48.
- Detected hashes: 184
- Domains: 38
- IPs detected: 8
- Industries: Finance, Manufacturing, Media And Entertainment, Banking, Energy And Natural Resources, Transportation, Information Technology, and Hospitality.
- Related Intrusion Methods: Obfuscation, Data Exfiltration, Data Breach, Social Engineering, Exfiltrate data, Credential Dumping, Malicious JavaScript, etc.
- Most recent sandbox reference: Hybrid Analysis
- Malware: Dridex, WastedLocker, BitPaymer, SocGholish, FriedEX, Cobalt Strike, Gozi and Gozi ISFB.
References detected
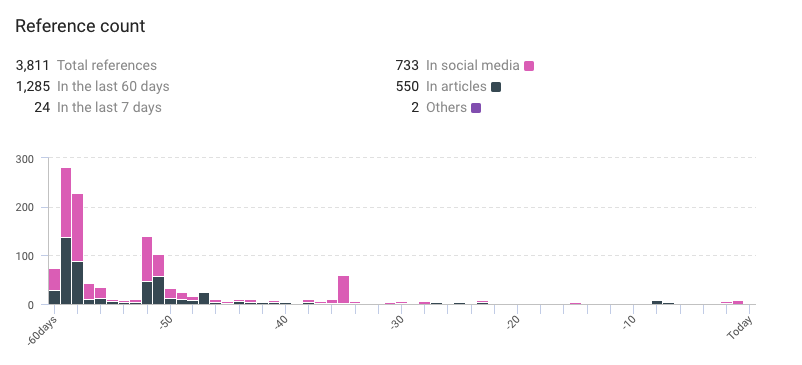
- Total references: 3,811
- References in the last 60 days: 1,285
- References in the last 7 days: 24.
#2 APT28 Fancy Bear
- Risk rules triggered: 7 out of 48.
- Detected hashes: 169
- Domains: 38
- Industries: Healthcare, Healthcare Providers, Sports, Media And Entertainment, Energy And Natural Resources, Aerospace And Defense, and Aviation.
- Most recent C&C server reference: Targeted malware with #NATO theme noticed last month
- Related Intrusion Methods: Phishing, Obfuscation, Phishing Campaign, Zero Day, Business Email Compromise, Spam, Password stealer, Jackpotting, etc.
- Most recent sandbox reference: Hybrid Analysis result for ‘tmp9e_7rbyv’
- Malware: Drovorub, Lojax, X-Agent, VPNFilter, Downdelph, CHOPSTICK, etc.
References detected
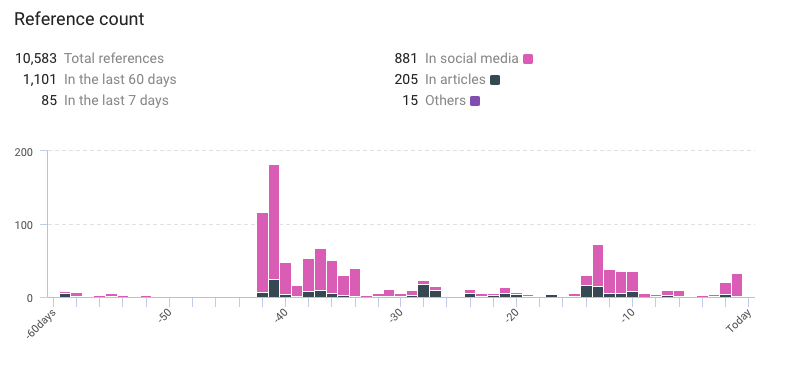
- Total references: 10,583
- References in the last 60 days: 1,101
- References in the last 7 days: 85
The beauty of KNOW is that you can gather all these references and context by just going through the story cards provided in your collated stories.
Netenrich Threat + Attack Surface Intelligence
KNOW is Netenrich’s Threat Intel Platform that extracts data from billions of data points and correlates relevant intel and expert analyst insights to help you follow, search, and act—in a fraction of the time it takes now. If you want to know more about KNOW then read this post about why we created the platform.
However, Netenrich’s offering isn’t just limited to threat intelligence. We offer a powerful combination of threat and attack surface intelligence. This combo helps SecOps to:
Threat and Attack Surface Intelligence will help your SecOps to:
- Find hidden risks to your brand on the public Internet
- Stay informed about threats in minutes versus hours
- Act on the most critical threats first.
- Reduce effort and alert fatigue.
- Measure and demonstrate value.
If you want to know more about Netenrich’s Attack Surface Intelligence (ASI), click here.
Subscribe To Our Newsletter!
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.
Thank you for subscribing!


