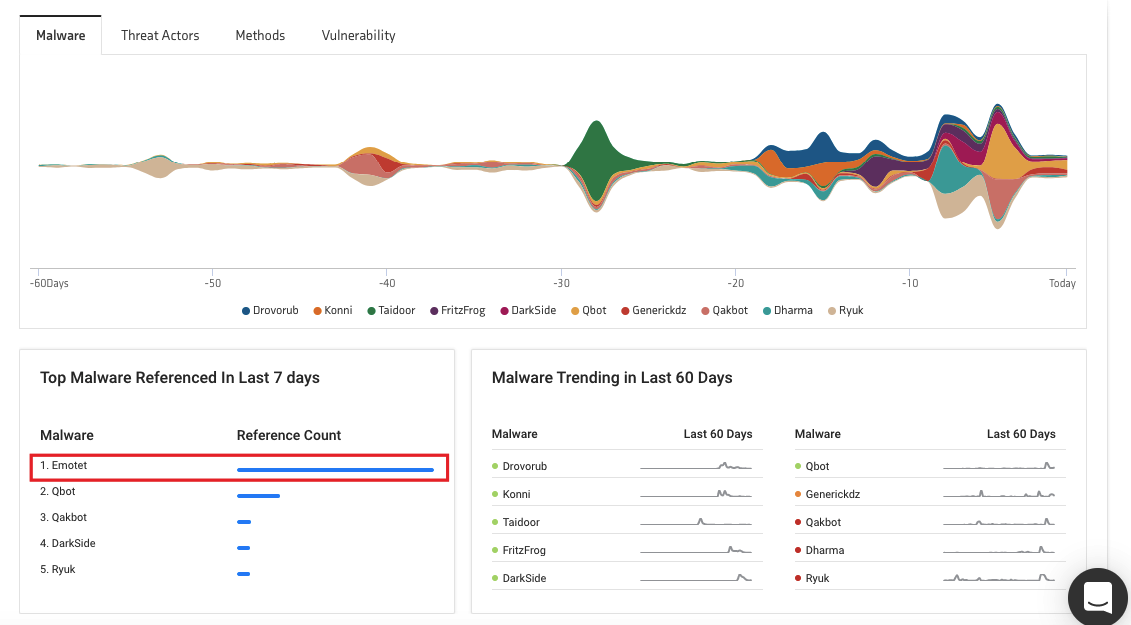
As detected by KNOW’s threat intel dashboard, Emotet is, by far, the most referenced malware of the last seven days.
Introduction to Emotet
Emotet, also known as Geodo and Mealybug, is a malware strain and a cybercrime operation. It was first detected in 2014 and primarily spread through spam emails.
These spam emails pretend to be invoices, shipping information, COVID-19 information, resumes, financial documents, or scanned documents. As with any other crimeware, Emotet’s goal is purely financial. Emotet delivers modular payloads to monetize infections. These payloads include:
- Godzilla loader
- Dridex
- Gootkit
- Qbot
- Qakbot
- BitPaymer
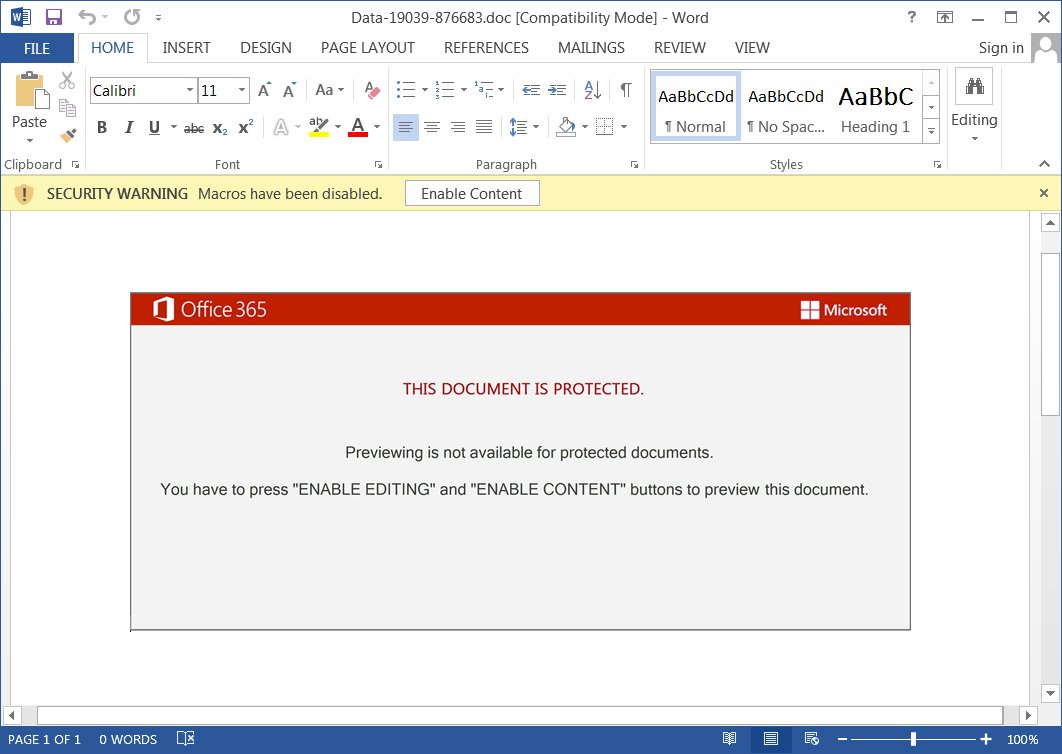
Emotet has been lately called the “Red Dawn” due to its doc attachment’s red accents.
Industries affected by Emotet
As per KNOW, Emotet has affected the following industries:
- Finance
- Manufacturing
- Media and entertainment
- Healthcare
- Education
- Banking
Threat actors taking advantage of Emotet
As per cybersecurity news, the infamous threat actor “TA542” has been prolifically using Emotet to install QBot. Along with that, Mummy Spider and Mealybug are two more well-known threat actors associated with the malware.
What do I do after getting hit by Emotet?
If you have been affected by Emotet, then you need to do two things asap:
- First, do not panic.
- Second, immediately isolate yourself from your network (if connected).
Isolation is essential because of the way Emotet has been designed to operate. Its sole purpose is to spread across all the connected systems as much as possible and hold your data hostage.
Once you have isolated, you need to patch and clean up your system immediately. To make sure that your network doesn’t get re-infected, each system needs to be isolated and patched. While this is definitely a very tedious process, it’s the only way to protect yourself against future Emotet attacks.
The best way to protect yourself against Emotet is to not get infected in the first place. The way that you can do that is by being proactive. Netenrich’s Attack Surface Intelligence (ASI) continuously monitors and protects your company, brand, and assets from external adversaries. Understand your exposure, prioritize risk, and remediate issues before they turn into incidents.
By the way, ASI also comes with a 30-day free trial wherein you can check how compatible it is with your systems. You can find out more here.
Thoughts from Twitter
@andpalmier:
#emotet seems quiet (for now), why not use this time to take down these domains? Some of them are active since July. Raw list: https://gist.github.com/andpalmier/848b8fb2a2a249047d16e17e37537bc4
@reach2ratan
TA542 Returns With Emotet: What’s Different Now http://dlvr.it/RfcfZf
@TripwireInc
Researchers observed that the Emotet gang had incorporated a new “Red Dawn” template into their weaponized Word Documents delivered to users.
What is KNOW?
KNOW is Netenrich’s Threat Intel Platform that extracts data from billions of data points and correlates relevant intel and expert analyst insights to help you follow, search, and act—in a fraction of the time it takes now.
One of KNOW’s handiest tools is the trending threats dashboard, which gives you a bird’s eye view of the most potent malware, threat actors, methods, and vulnerabilities in the following time frames:
- Last 7 days.
- Last 60 days.
So, want to check out KNOW some more? Why don’t you sign up? It’s completely free.
Subscribe To Our Newsletter!
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.
Thank you for subscribing!