APT 29, aka Cozy Bear, a Russian state-backed threat actor group, has been deemed responsible for a series of attacks on the US government. The attacks were so severe that it caused an emergency National Security Council meeting at the White House. Cozy Bear was previously responsible for hacking the US State Department and the White House during the Obama administration.
How did Cozy Bear hack the US Government?
APT 29 allegedly tampered with the updates released by SolarWinds – an IT company that serves government customers across the executive branch, the military, and the intelligence services. Specifically, they compromised SolarWinds’ Orion monitoring and management software.
This attack, aka “supply chain attack,” works by hiding malicious code in the body of legitimate software updates provided by third-parties. Among several things, these attackers were responsible for:
- Monitoring internal email traffic in the U.S. Treasury and Commerce departments.
- Conducting a security breach at FireEye.
- Targeting COVID-19 vaccine research
US and Russia react to the Cozy Bear hack
The US government has not publicly disclosed any information beyond the Commerce Department confirming that they have suffered a breach, currently under investigation by the Cybersecurity and Infrastructure Security Agency (CISA) and the FBI. John Ullyot of the National Security Council ensured that they “are taking all necessary steps to identify and remedy any possible issues related to this situation.”
The Russian foreign ministry was quick to dismiss the allegations as wholly baseless. The ministry posted the following on their Facebook page:
“We declare responsibly: malicious activities in the information space contradict the principles of the Russian foreign policy, national interests and our understanding of interstate relations. Russia does not conduct offensive operations in the cyber domain.”
Join 1,200 of your colleagues and friends from the industry
Twitter reacts to Cozy Bear
#1 Alyza Sebenius
As government agencies + private companies rush to assess the damage from a global cyberattack with a sweeping list of victims, a prime suspect is the Russia-linked group APT 29. Previously, the group targeted the DNC in 2016 + Covid-19 research this year.https://t.co/006nResXbI
— Alyza Sebenius (@asebenius) December 15, 2020
#2 Andy Greenberg
Some here pointing to the SolarWinds hack as the other Sandworm/NotPetya shoe dropping. Still early, but this looks like targeted spying as you'd expect from APT29/SVR, not Sandworm/GRU-style disruption. Not yet sure it's less serious, just very different. https://t.co/2MwIRsmprT
— Andy Greenberg (@a_greenberg) December 14, 2020
#3 Ellen Nakashima
BREAKING: Russian hacking group APT29 behind broad espionage campaign that breached Treasury, Commerce, FireEye.
— Ellen Nakashima (@nakashimae) December 13, 2020
#4 Zev Shalev
Russia's hacker group APT 29 breached the U.S. Depts of Commerce and Treasury. The attacks come just weeks after the nation's top cybersecurity official Chris Krebs was fired by Donald Trump for rejecting his claims of widespread election fraud. https://t.co/v2QGi5ScoW
— Zev Shalev (@ZevShalev) December 13, 2020
SolarWinds releases statement on Cozy Bear attack
According to SolarWinds, the updates released between March and June 2020 were compromised by a “highly-sophisticated, targeted, and manual supply chain attack by a nation-state.” SolarWinds has an enviable client list that includes most of America’s Fortune 500 companies, the top 10 U.S. telecommunications providers, all five branches of the U.S. military, the State Department, the National Security Agency, and the Office of President of the United States. This attack has understandably caused a panic within the US intelligence community since it exposes various government agencies to the risk.
Netenrich’s CISO Brandon Hoffman, broke down why tools like SolarWinds are perfect targets for hackers:
“There is a digitally signed component of SolarWinds that has a flaw allowing anybody to write to an executable. This essentially comes down to improper privilege management in a tool that is deeply embedded into system administration. Adversaries who weaponized this flaw allowed them to leverage all the capability of a remote management solution. The reason these systems are good targets is because they are deeply embedded in systems operations and administration.”
John Bambenek, President of Bambenek Consulting, believes that it’s highly probable that the hackers compromised SolarWinds by taking over their private key. If that’s the case, then this could be just the tip of the proverbial iceberg. As Bambenek puts it:
“If the private key is compromised, they can’t issue an update until a new private key proves its trustworthiness.”
How threat intelligence prepares you for threat actors like Cozy Bear
Cybersecurity is incomplete without accurate threat intelligence. KNOW, Netenrich’s free and comprehensive threat intel platform, collects intelligence from technical sources and billions of data points across several million online sources and open source threat intelligence (OSINT).
Receive critical context for immediate action, monitor active & relevant threats, and get the latest threat intelligence news and look up indicators directly from your mobile phone.
Let’s find out what KNOW has to say about Cozy Bear.
Cozy Bear references from KNOW
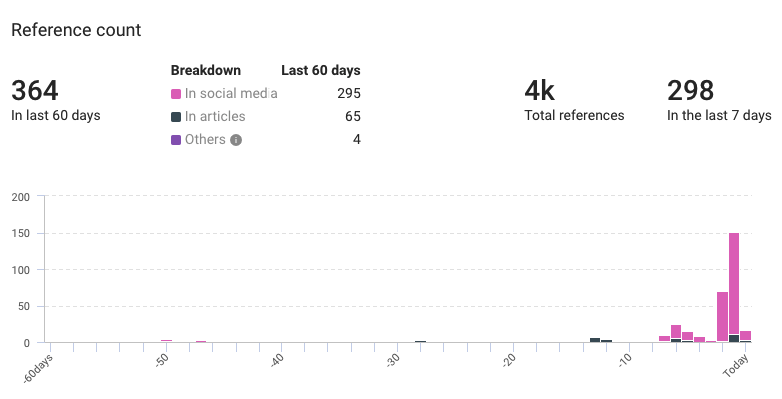
- Total references: 4,000
- Last 60 days: 364
- Previous 7 days: 298
Cozy Bear context from KNOW
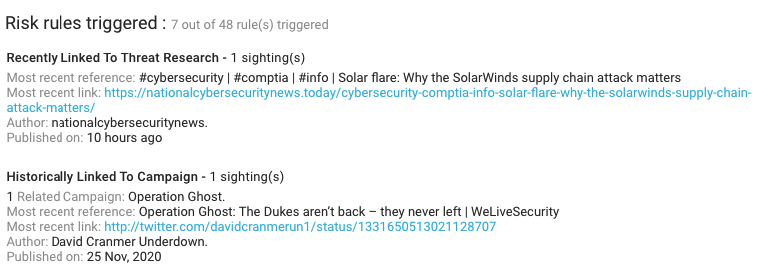
- Risk rules triggered: 7 out of 48
- Campaign: Operation Ghost
- Hashes: 35
- Industries affected: industries: Healthcare, Energy & Natural Resources, Healthcare Providers, Finance, Aerospace & Defense, Education, and Research
- Most recent sandbox sighting: Hybrid Analysis result for ‘Tracking GhostNet_ Investigating Cyber Espionage – Network Information Warfare Monitor.pdf’
- Related intrusion methods: Phishing, Web shell, Data Exfiltration, Social Engineering, Privilege Escalation, Spam Campaign, Directory Traversal and 14 more
- Malware: WellMail, WellMess, OnionDuke, MiniDuke, RegDuke, PolyglotDuke, PoisonIvy, Cloudlook, SOGU, and njRAT
- Vulnerabilities: CVE-2019-11510, CVE-2018-13379, CVE-2019-19781, and CVE-2019-9670
Secure your systems with a 1-2 punch of threat and attack surface intelligence

Companies invest thousands (conservatively) in firewalls, SIEMs, anti-malware, Intrusion Prevention/ Detection Systems (IPS/IDS), and other security tools. Yet, they produce gazillions of alerts, most of which turn out to be false positives. Netenrich delivers a powerful combination of Threat and Attack Surface Intelligence led by machines and powered by security experts.
Empower your SecOps to:
- Find hidden risks to your brand on the public Internet
- Stay informed about threats in a minute versus hours
- Act on the most critical threats first
Interested?
YES I AMOh and since you are here, why don’t you check out our latest article on how you can turn 2020’s cybersecurity challenges into next year’s opportunities?
SHOW ME
Subscribe To Our Newsletter!
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.
Thank you for subscribing!


