Netenrich’s news aggregator, KNOW, serves up the latest security stories for a bird’s-eye view of the global threat landscape. The main news section of KNOW can be accessed here.
When you go to the “malware” section, you see trending stories:
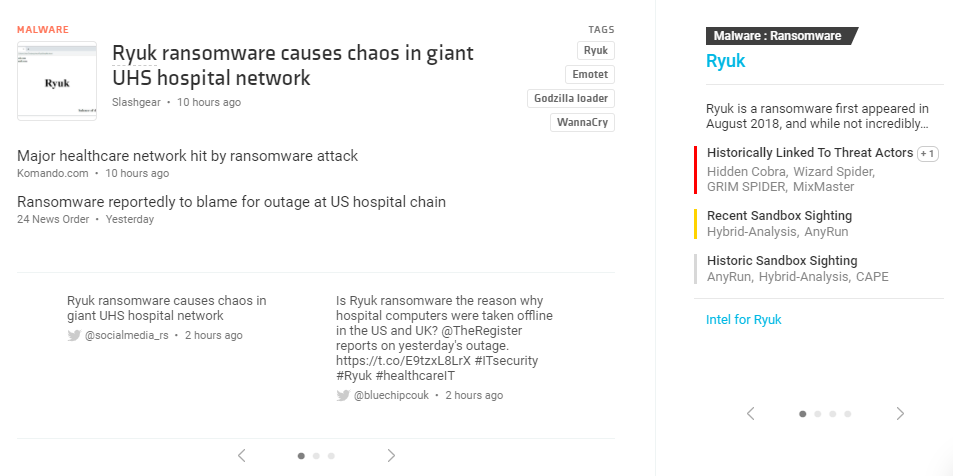
Let’s take a closer look at the story mentioned above.
Universal Health Services hospitals across the country abruptly shutdown. UHS confirmed it has an IT security issue that forced it to take its computer networks offline but didn’t confirm or deny that it was related to ransomware. Employee testimonies, however, pointed to how files were being renamed with the “.ryk” extension that has been associated with the Ryuk ransomware.
Ryuk was originally attributed to North Korean actors but was later believed to have originated from Russia instead. The main actor for the ransomware seems to have faded into the background last April but has apparently resurfaced. But while many ransomware cybercriminals vowed not to touch hospitals, Ryuk’s users had no such qualms.
Malware detected by KNOW
KNOW has collated all the related malware associated with this particular attack. In this case, we have:
- Ryuk
- Godzilla Loader
- WannaCry
Along with this, it provides enough contextual data for your security team to study so that they have enough context to make informed decisions. So, let’s see what info KNOW has collected for us.
#1 Ryuk
Ryuk is a ransomware first appeared in August 2018, and while not incredibly active across the globe, at least three organizations were hit with Ryuk infections over the course of the first two months of its operations, landing the attackers about $640,000 in ransom for their efforts. Ryuk itself possesses functionality that you would see in a few other modern ransomware families. This includes the ability to identify and encrypt network drives and resources, as well as delete shadow copies on the endpoint. By doing this, the attackers could disable the Windows System Restore option for users, and therefore make it impossible to recover from the attack without external backups.
Industries targetted:
- Healthcare
- Energy and natural resources
- Hospitals
- Education
- Media and entertainment
- Information technology
References counted by KNOW:
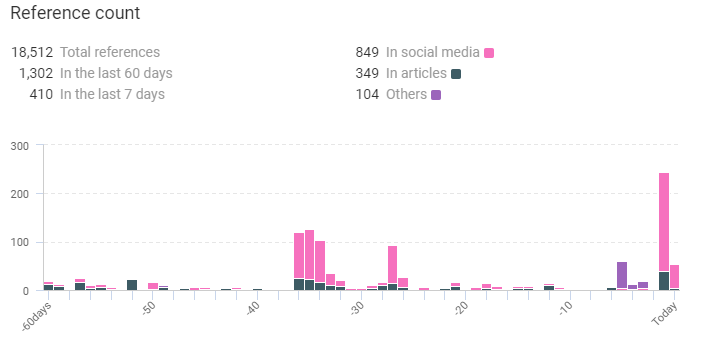
Along with it, KNOW also collected the following data regarding Ryuk:
BleepinComputer: An employee told BleepingComputer that, during the attack, files were being renamed to include the .ryk extension. This extension is used by the Ryuk ransomware. https://t.co/xoy2HXFrVQ #cybersecurity #hacking #computersecurity #nyc #newyork
— Cyber Secure New York (@cybersecureny) September 28, 2020
UHS Hospitals Across the United States Reportedly Impacted by Ryuk Ransomware https://t.co/QlIl78bqWW
— IT Security News – www.itsecuritynews.info (@IT_securitynews) September 28, 2020
#ransomware | #computerhacker | RYUK virus running riot as it strikes down another victim in Tower https://t.co/8SBRUgE2pB
— National Cyber Security (@NcsVentures) September 8, 2020
#2 Godzilla Loader
The malware Godzilla loader was first discovered in May 2016 and was used to deliver the infamous TrickBot banking trojan. It targets computers running Windows operating system. A new version of Godzilla Loader was found on Dark Web forums. Cybercriminals Advertising Godzilla Loader Malware for $500 on Dark web forums, the malware found actively maintained and getting new updates periodically. It comes with a built-in UAC bypass, includes a full plugin ecosystem, a propagation module, a keylogger module, and a password-stealing module. Godzilla Loader’s functionalities are similar to that of the Emotet banking trojan. The malware is delivered via phishing emails. The latest Godzilla Loader variant developed in December 2017 uses RSA-2048 to verify the identity of the Communication & Control server. The latest variant comes with enhanced security layer which makes the C2 communication safe and had more control flow to fully rely on the Component Object Model (COM) interfaces.
Industries targetted:
- Finance
- Banking
- Education
- Healthcare
- Telecommunications
- Research
Reference counted by KNOW:
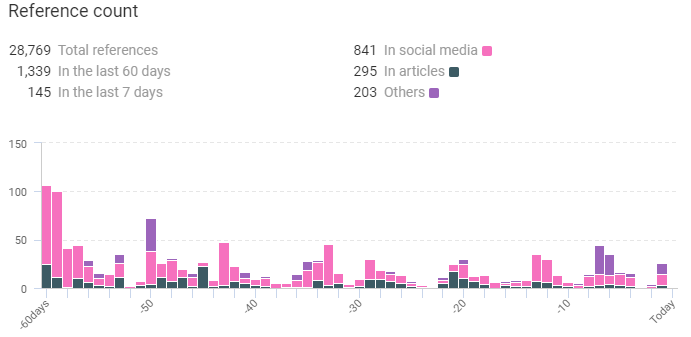
Along with it, KNOW also collected the following data regarding Godzilla Loader:
#3 WannaCry
WannaCry is a ransomware worm that spread rapidly through across a number of computer networks in May of 2017. After infecting Windows computers, it encrypts files on the hard drive, making them difficult for users to access,. It then demands a ransom payment in bitcoin to decrypt them.
Numerous factors made the initial spread of WannaCry particularly noteworthy. It struck various crucial and high-profile systems, including Britain’s National Health Service; it exploited Windows vulnerability that was suspected to have been first discovered by the US National Security Agency; and it was linked by Symantec and other security researchers to the Lazarus Group, a cybercrime organization that could be connected to the North Korean government.
Industries targetted:
- Banking
- Healthcare
- Electronics
- Medical device
- Finance
- Education
Reference counted by KNOW:
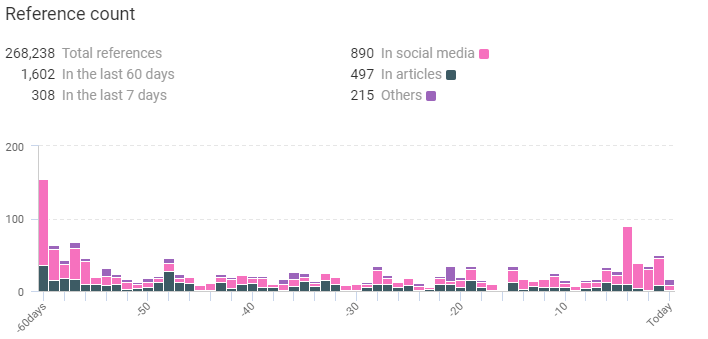
Along with it, KNOW also collected the following data regarding WannaCry
What is KNOW?
KNOW is Netenrich’s Threat Intel Platform that extracts data from billions of data points and correlates relevant intel and expert analyst insights to help you follow, search, and act—in a fraction of the time it takes now.
One of KNOW’s handiest tools is the trending threats dashboard, which gives you a bird’s eye view of the most potent malware, threat actors, methods, and vulnerabilities in the following time frames:
- Last 7 days.
- Last 60 days.
So, want to check out KNOW some more? Why don’t you sign up? Did we mention that it’s completely free?
Or subscribe to get daily threat intel updates.
Subscribe To Our Newsletter!
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.
Thank you for subscribing!




