The US government has finally decided to blame Russia for the infamous SolarWinds attack. As per the report, the hack was an “intelligence gathering effort” by Cozy Bear – the threat actor responsible with ties to the Kremlin. This was one of the top trending stories as collated by KNOW – our cybersecurity news aggregator and threat intel platform.
How did the SolarWinds attack happen?
The hackers infiltrated SolarWinds’ Orion Software by injecting trojan malware. By doing so, the hackers could spy on multiple government agencies like the US Treasury, State Department, and the Department of Homeland Security. They also managed to infiltrate Microsoft products and cloud service provider VMware.
Aftermaths of the SolarWinds attack
SolarWinds has been sued by an investor who claimed that the firm was aware of the vulnerability but didn’t take any steps to remediate it. Meanwhile, the US National Security Council created a new task force named the “Cyber Unified Coordination Group” (UCG). They will be responsible for investigating the SolarWinds attack and lead remediation efforts. As per the authorities:
“The UCG remains focused on ensuring that victims are identified and able to remediate their systems, and that evidence is preserved and collected. Additional information, including indicators of compromise, will be made public as they become available.”
Reactions from Twitter
#1 CISA
Just released: Joint statement with our partners at @FBI, @ODNIgov, and @NSAGov on the recent significant cyber incident involving federal government networks: https://t.co/nxHaN5UJRp
— Cybersecurity and Infrastructure Security Agency (@CISAgov) January 5, 2021
#2 Carla Gentry
The US government has accused Russia of being behind the recent SolarWinds attack, which is considered to be among the most significant of 2020. https://t.co/Fnrq2YUG8q
— Carla Gentry (@data_nerd) January 6, 2021
#3 ZDNet
US government formally blames Russia for SolarWinds hack https://t.co/RMo2LugB3m
— ZDNet (@ZDNet) January 6, 2021
SolarWinds attack context from KNOW
KNOW attaches automated threat context to the stories it collates. In this story, it has attached context for Sunburst and APT 29 aka Cozy Bear.
#1 What is Sunburst?
Sunburst is a trojanized version of SoalrWinds.Orion.Core.BusinessLayer.dll of Solarwind Orion IT monitoring tool. The trojanized file delivers the SUNBURST malware through a backdoor as part of a digitally-signed Windows Installer Patch.
Industries targeted
- Information Technology
- Consulting
- Telecommunications
- Cybersecurity
Sunburst references from KNOW
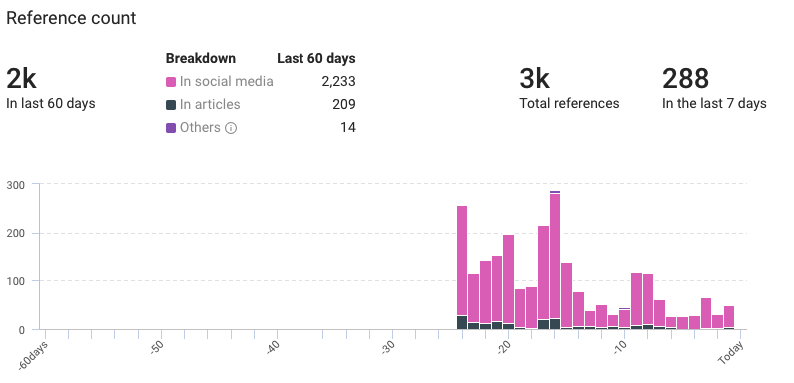
- Total references: 3,000
- Previous 60 days: 2,000
- Last 7 days: 288
Sunburst context from KNOW
- Related intrusion methods: Data Exfiltration, Computer Network Exploitation, Steganography.
- Associated threat actors: APT29 The Dukes and UNC2452
- IPs: 7
- Domains: 5
- Hashes: 17
- URLs: 1
- Most sandbox sighting: Hybrid Analysis result for ‘876a6b9a546cade33fc5665c11911fb1722a6763196fdbee5fa720f2f8baac23’
#2 More on Cozy Bear
Prior to this attack, Cozy Bear’s victims primarily belonged to Western Europe, Brazil, China, Japan, Mexico, New Zealand, South Korea, Turkey, and Central Asian countries.
Cozy Bear references from KNOW

- Total references: 4,000
- Last 60 days: 364
- Previous 7 days: 298
Cozy Bear context from KNOW

- Risk rules triggered: 7 out of 48
- Campaign: Operation Ghost
- Hashes: 35
- Industries affected: industries: Healthcare, Energy & Natural Resources, Healthcare Providers, Finance, Aerospace & Defense, Education, and Research
- Most recent sandbox sighting: Hybrid Analysis result for ‘Tracking GhostNet_ Investigating Cyber Espionage – Network Information Warfare Monitor.pdf’
- Related intrusion methods: Phishing, Web shell, Data Exfiltration, Social Engineering, Privilege Escalation, Spam Campaign, Directory Traversal and 14 more
- Malware: WellMail, WellMess, OnionDuke, MiniDuke, RegDuke, PolyglotDuke, PoisonIvy, Cloudlook, SOGU, and njRAT
- Vulnerabilities: CVE-2019-11510, CVE-2018-13379, CVE-2019-19781, and CVE-2019-9670
Secure your systems with a 1-2 punch of threat and attack surface intelligence

Companies invest thousands (conservatively) in firewalls, SIEMs, anti-malware, Intrusion Prevention/ Detection Systems (IPS/IDS), and other security tools. Yet, they produce gazillions of alerts, most of which turn out to be false positives. Netenrich delivers a powerful combination of Threat and Attack Surface Intelligence led by machines and powered by security experts.
Empower your SecOps to:
- Find hidden risks to your brand on the public Internet
- Stay informed about threats in a minute versus hours
- Act on the most critical threats first
Interested?
YES I AMOh and since you are here, why don’t you check out our latest article on how you can turn 2020’s cybersecurity challenges into next year’s opportunities?
SHOW ME
Subscribe To Our Newsletter!
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.
Thank you for subscribing!




