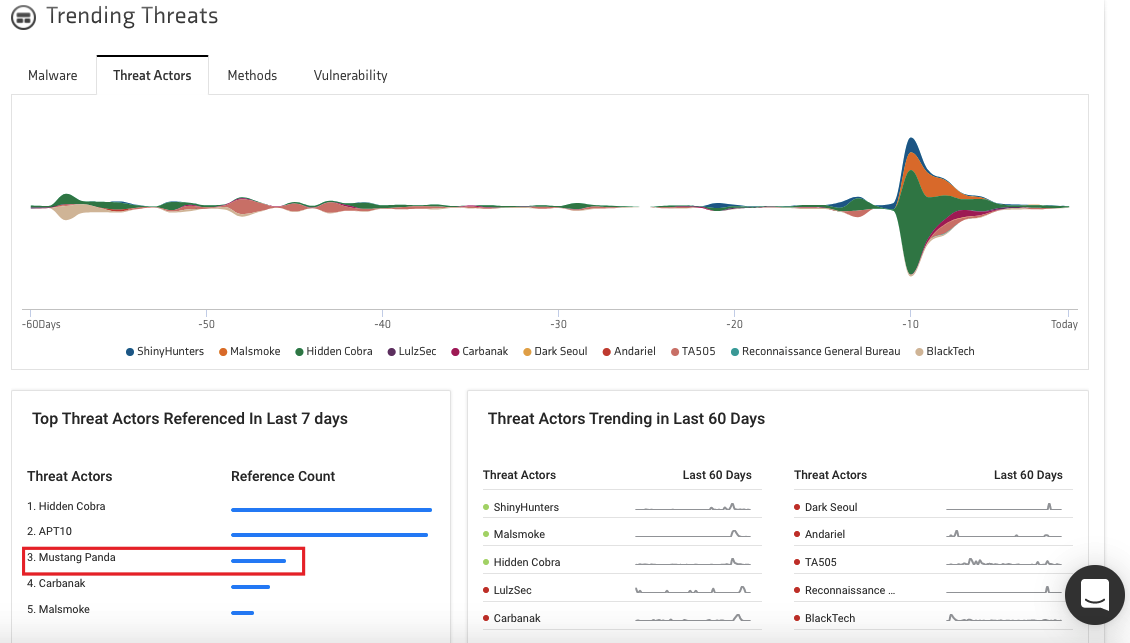
Today we are going to be focussing on a China-based threat actor – Mustang Panda. As per KNOW, our threat intel dashboard and cybersecurity news aggregator, Mustang Panda, was the third most trending threat actor over the last seven days.
Mustang Panda: Who are they?
Mustang Panda primarily targets non-governmental organizations (NGOs). It uses Mongolian language decoys and themes and attacks its targets with shared malware like Poison Ivy or PlugX. Their attack chain looks something like this:
- A malicious link is sent to a Google Drive folder, cloaked using the goo.gl link shortening service.
- When clicked on, the Google Drive link fetches a zip file, containing a .Ink file cloaked as a .pdf file.
- Upon opening the file, it redirects the user to a Windows Scripting Component (.wsc) file. This file is hosted on a malicious microblogging page.
- The .Ink file has an embedded VBScript to retrieve the decoy PDF file and a PowerShell script from the microblogging page.
- The PowerShell script prepares a Cobalt Strike (https://know.netenrich.com/threatintel/malware/Cobalt%20Strike) payload.
- Cobalt Strike connects with the command-and-control IP address allowing the threat actor to control the system remotely.
Why is Mustang Panda trending?
Security researchers have recently detected a resurgence of Mustang Panda activity. As of now, their target appears to be the Chinese Catholics. The hackers are targeting the group with an email phishing campaign. They have spoofed the Catholic journalists’ email headers in their phishbait.
Reactions from Twitter
#1 Security Week
Chinese Threat Actor 'Mustang Panda' Updates Tools in Attacks on Vatican https://t.co/nA1vL2b0uv
— SecurityWeek (@SecurityWeek) November 25, 2020
#2 Virus Bulletin
Proofpoint researchers analysed recent activity by the China-linked TA416 (Mustang Panda) APT group, which used a new Golang variant of the PlugX malware against targets linked to Myanmar and the Vatican https://t.co/pJdKR2fSGm pic.twitter.com/hjHgR5cpTS
— Virus Bulletin (@virusbtn) November 24, 2020
#3 Threatpost
The TA416 APT was spotted launching spear-phishing attacks with a never-before-seen #Golang variant of its PlugX #malware loader.https://t.co/zeXEfEaDTn
— Threatpost (@threatpost) November 24, 2020
Mustang Panda references from Twitter
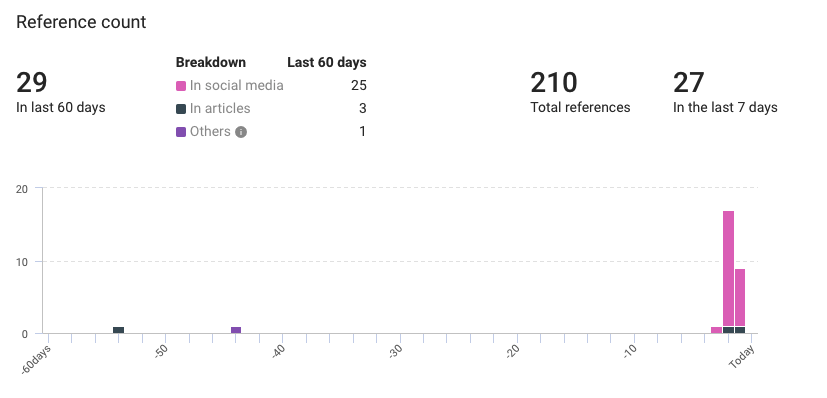
- Total references: 210
- Last 60 days: 29
- Previous 7 days: 27
Mustang Panda context from KNOW
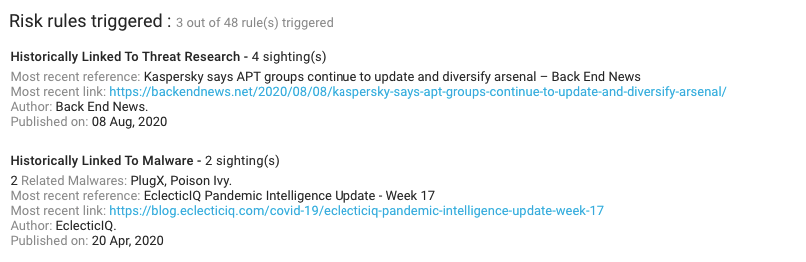
- Risk rules triggered: 3 out of 48
- Malware associated: PlugX and Poison Ivy.
- Most recent sandbox reference: Any Run Sandbox result for 86590f80b4e1608d0367a7943468304f7eb665c9195c24996281b1a958bc1512
Stopping Mustang Panda with Threat and Attack Surface Intelligence
KNOW is our threat intel and news-aggregator platform that allows you to gain the latest context of the hottest news in the global threatlandscape.
Your SecOps and IT Ops teams are continually observing your network 24*7, yet adversaries like FIN11 always manage to go through. To be fair, it’s not really their fault because current risk models cause them to chase false positives instead of tracking business-critical threats.
Netenrich’s resolution intelligence uses a combination of threat and attack surface intelligence that effectively addresses the following pain points:
- Your organization’s attack surface is growing faster than your SecOps team and budget.
- Threat actors can see exposed assets that lie outside your security’s purview.
- There is a severe lack of talent and skill gaps is getting wider than ever before.
- Attacks are more frequent and it only takes one to inflict severe, irreversible damage on your organization and business reputation.
Resolution intelligence is a powerful combination of machine and human intel that helps your SecOps to:
- Find hidden risks in your brand.
- Prioritize business-critical alerts.
- Stay informed about the most trending threats.
- Reduce alert fatigue by a considerable amount.
Do you want to know how we do all this? Well, first, you should subscribe to KNOW. Don’t worry. It’s completely free.
Alright, I will subscribe.Next, you should know more about what resolution intel brings to the table. So, click on the button below to read up on it.
Awesome, let's do it
Subscribe To Our Newsletter!
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.
Thank you for subscribing!





