Netenrich’s KNOW is a news aggregator serving up the latest, hottest-trending security stories of the moment for a bird’s-eye view of the global threat landscape. The main news section of KNOW can be accessed here.
When you go to the “malware” section, you see trending stories:
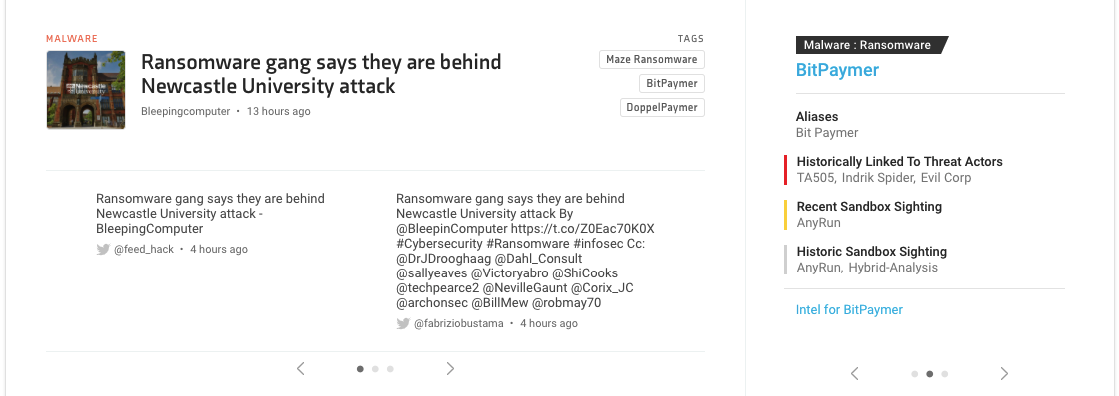
Let’s take a closer look at the story mentioned above.
UK research university Newcastle University was badly hit by DoppelPaymer ransomware, which took the systems offline on August 30th. The university released a statement saying that the attack was so bad, it will “take several weeks to address.”
So, what was the extent of this attack? All university systems, not comms related, were unavailable or “available with limitation.” As you can imagine, this caused unprecedented operational disruption across their networks and IT systems.
Malware detected by KNOW
KNOW has collated all the related malware associated with this particular attack. In this case, we have:
- DoppelPaymer.
- Maze.
- BitPaymer
Along with this, it provides enough contextual data for your security team to study so that they have enough context to make informed decisions. So, let’s see what info KNOW has collected for us.
#1 DoppelPaymer
DoppelPaymer is a ransomware known for attacking enterprise targets. It gains access to systems via admin creds and uses them to compromise the whole system. It has been active since mid-July 2019.
Industries targetted:
- Aerospace and defense
- Manufacturing
- Healthcare
References counted by KNOW:
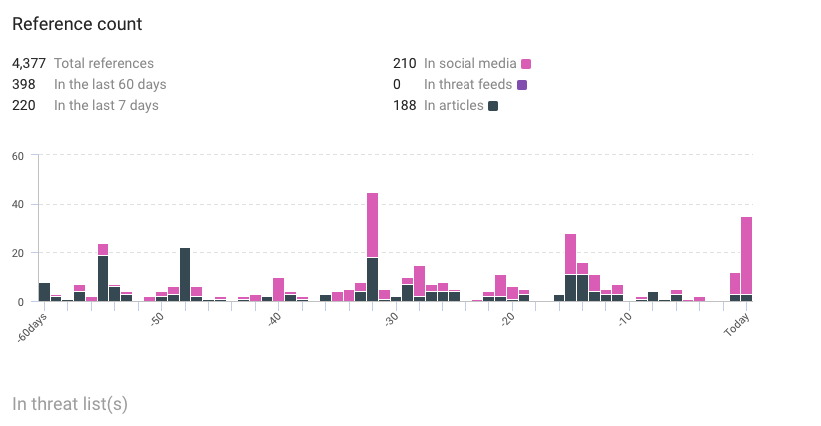
- Total: 4,377.
- Last 60 days: 398.
- Last 7 days: 220.
Along with it, KNOW also collected the following data regarding DoppelPaymer:
- Risk rules triggered: 5 out of 48.
- Vulnerabilities: CVE-2019-1978 and CVE-2019-19781
- Threat Actors: TA505 and Indrik Spider
- Historic Sandbox Sighting: AnyRun, Hybrid-Analysis, and CAPE.
Twitter’s thoughts on DoppelPaymer
@cybsploit
Doppelpaymer Ransomware was not distributed via Bluekeep Exploit #Doppelpaymer #Cryptominer #Botnet #Network #BlueKeep #RansomWare
@AuCyble
#DopplePaymer #Ransomware Operators Allegedly Struck Royal Military College of Canada
#2 BitPaymer
BitPaymer is a well-known malware that was first seen in January 2016.
Reference counted by KNOW:
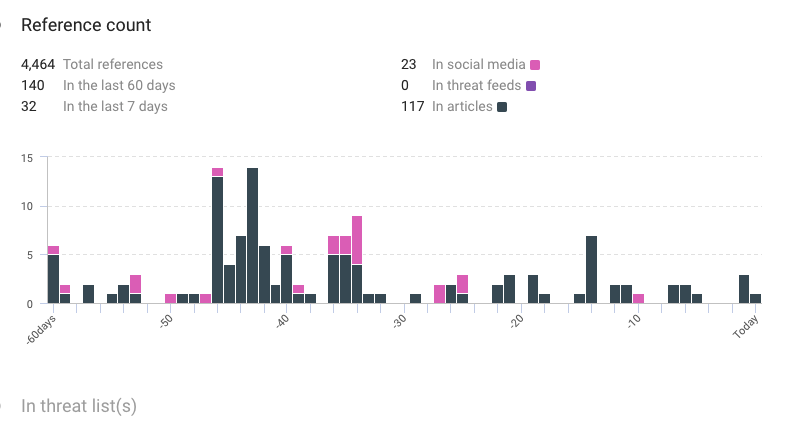
- Total: 4,464
- Last 60 days: 140
- Last 7 days: 32
Along with it, KNOW also collected the following data regarding BitPaymer:
- Risk rules triggered: 2 out of 48.
- Threat Actors: TA505, Indrik Spider, Evil Corp.
- Recent Sandbox Sighting: AnyRun.
- History Sandbox Sighting: AnyRun and Hybrid-Analysis.
Twitter’s thoughts on BitPaymer
@Ben_P9T RT
Webroot ““Top-tier campaigns like Bitpaymer and Ryuk ransomware, or Trickbot and dridex Trojans—these are all going to get past a lot of built-in antivirus software.”
@campuscodi
Department of Treasury wouldn’t comment why EvilCorp’s “BitPaymer” ransomware wasn’t listed on the sanctions page, but only Dridex.
A lawyer told me this was an intentional loophole in the sanctions to allow for ransom payments and avoid crippling US companies for good.
#3 Maze
Maze is a particularly sophisticated strain of Windows ransomware that has hit companies and organizations around the world. Maze ransomware was first discovered in 2019 and was initially distributed via spam emails and exploit kits before shifting to being deployed post-compromise.
The ransomware’s main goal is to encrypt all files that it can in an infected system and then demand a ransom to recover the files. It also maintains a public-facing website where they post data stolen from victims who refuse to pay an extortion fee. In April 2020, it hit IT services giant Cognizant, causing service disruptions.
Industries
- Finance
- Healthcare
- Information technology
- Computer hardware
- Consumer electronics
- Insurance
Reference count
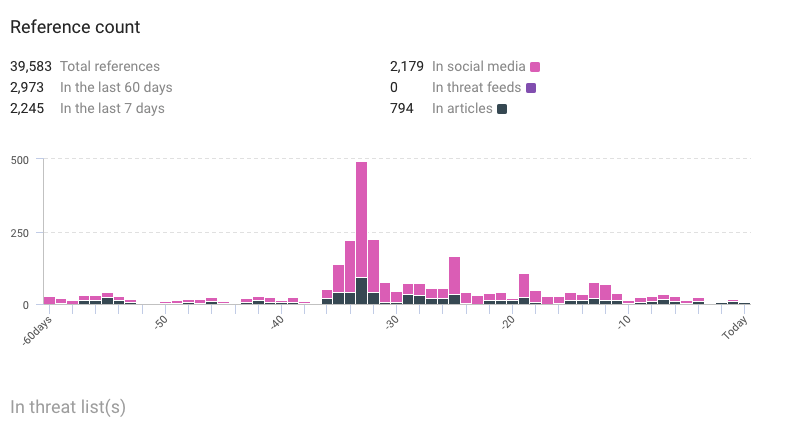
- Total: 39,583
- Last 60 days: 2,965
- Last 7 days: 2,237
Along with it, KNOW also collected the following data regarding Maze
- Associated IPs: 37
- Associated Domains: 107
- Associated Hashes: 160
- Associated URLs: 878
- Risk rules triggered: 7 out of 48
- Vulnerabilities detected: CVE-2018-4878 CVE-2018-8174 CVE-2018-15982 CVE-2019-11510 CVE-2019-19781
- Related Threat Actors: AnonSec APT1 Comment Crew FIN6 Anonymous APT41 TA2101
Twitter’s thoughts on Maze
@AuCyble
One of the World’s Largest Chipmakers Got Allegedly Breached By #Maze #Ransomware Operators.
@feed_hack
Canon hit by Maze Ransomware attack, 10TB data allegedly stolen – BleepingComputer
What is KNOW?
KNOW is Netenrich’s Threat Intel Platform that extracts data from billions of data points and correlates relevant intel and expert analyst insights to help you follow, search, and act—in a fraction of the time it takes now.
One of KNOW’s handiest tools is the trending threats dashboard, which gives you a bird’s eye view of the most potent malware, threat actors, methods, and vulnerabilities in the following time frames:
- Last 7 days.
- Last 60 days.
So, want to check out KNOW some more? Why don’t you sign up? Did we mention that it’s completely free?
Or subscribe to get daily threat intel updates.
Subscribe To Our Newsletter!
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.
Thank you for subscribing!




