Cybercriminals are known to flourish in times of crisis, like the current COVID-19 pandemic. Social engineering attacks are running rampant, as threat actors prey on the turmoil introduced by the disruption. With people staying home more, there’s a steep rise of financial information being transmitted electronically and more chances of cyber attacks. Security teams are finding it hard to keep track of the biggest malware threats out there, and identifying ways to protect the business.
Ever wondered if it could be easier to keep up with all the cyber news and threats that you care about? If scanning hundreds of blogs, social media, web, and OSINT feeds, is getting tiresome, then look no further. KNOW from Netenrich aggregates news on cyber attacks and is the first-of-its-kind, FREE global threat intelligence tool.
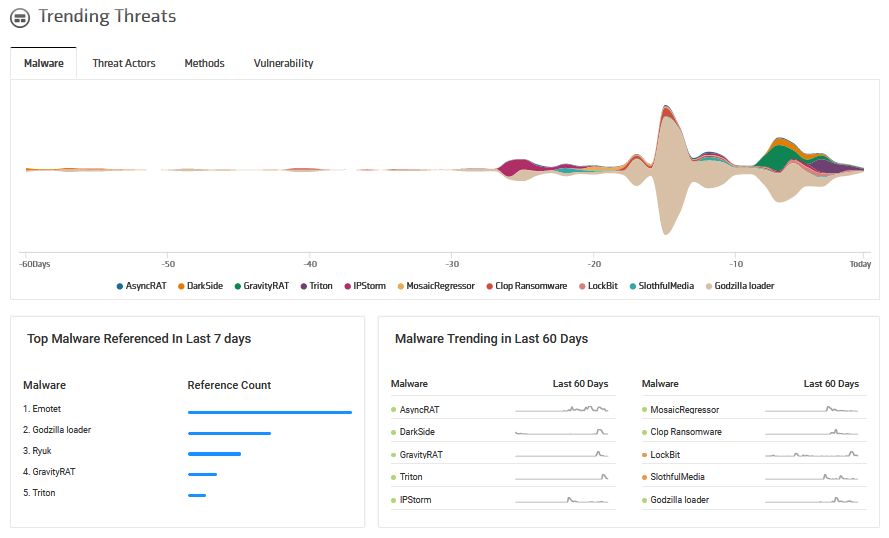
Trending malware detected by KNOW
Knowledge NOW aka KNOW collects information on cyber threats and adds contextual data for your security team to study, so you can save time on research and focus on ensuring proactive cybersecurity.
Today we’re going to dig deep into the “Trending Threats” section in KNOW, and get insights for the top malware referenced over the last 60 days.
GravityRAT
GravityRAT is a malware allegedly designed by Pakistani hackers. It’s built to infiltrate computers and steal the data of users and relay the stolen data to Command and Control centers in other countries. It was first detected by Indian Computer Emergency Response Team, CERT-In in 2017. GravityRAT has now become self-aware and can evade several commonly used malware detection techniques.
What does it do?
GravityRAT infiltrates a system by pretending to be a harmless email attachment, which can be in any format, including MS Word, MS Excel, MS Powerpoint, Adobe Acrobat or even audio and video files. The new version of GravityRAT can check system temperature by recording thermal readings for detecting the presence of VMs (virtual machines). It can also collect open ports on the targeted system and creates a list of all the active processes after which it starts stealing files stored on any connected USB drive.
Malware threat intel from KNOW:
- Recently Linked To Threat Research – 2 sighting(s)
- Historically Linked To Threat Actors – 1 sighting – APT34 Oilrig
- Historically Linked To Intrusion Method – Remote Command Execution, Remote code execution, Denial Of Service, Cryptojacking, Infection chain, Exploit.
- Historically Linked To C&C Server – 7 sighting(s)
- Historic Sandbox Sighting – 14 sightings.
- Most recent reference: Any Run Sandbox result for Q.Whisper.exe
Additional threat intelligence from our experts at the Netenrich Threat Research Center:
Target: Microsoft Windows, Android, MacOS
Method: Powershell Invoke, VBS Script,
Functionalities: Data Stealing, AES Encryption, Information Discovery
Uses: HTTP for C2 Communication
MD5: f06a062060a7273b2919ab9937a56473 , 085c347a3c338db94b791feca9a1881a
Track GravityRATIPStorm
The name IPStorm is the abbreviation of InterPlanetary Storm that emerged from the InterPlanetary File System (IPFS.) It’s a peer-to-peer protocol used by the bot for communications with the intent to obscure the malicious traffic.
The bot was written in the Go programming language, initially created to compromise Microsoft Windows systems only. Security firms have recently discovered new IPStorm versions that are able to target also Android, Linux, and Mac.
What does it do?
Security experts report that IPStorm was infecting Android systems with ADB (Android Debug Bridge) port exposed online. The bot can target Linux and Mac devices to perform dictionary attacks against SSH services to guess username and passwords.
Once a connection is established, the malware checks the presence of a honeypot by comparing the hostname of the attacked server to the string “svr04”, which is the default hostname of Cowrie SSH honeypot. The IPStorm bot also kills a list of processes that could potentially interfere with its operations. Its versions for both Linux and Windows systems implement a reverse shell mechanism, however, researchers have not seen the IPStorm operators engaging in malicious activities, such as performing DDoS attacks or relaying malicious traffic.
Malware threat intel from KNOW:
- Recently Linked To Threat Research – 2 sighting(s)
- Historically Linked To Threat Actors: BuggiCorp.
- Historically Linked To Intrusion Method: SSH Brute Force.
- 706 Reference(s) to this entity: First seen 11 Jun, 2019, Last seen 26 Oct, 2020
Additional threat intelligence from our experts at the Netenrich Threat Research Center:
Language: Go
Target: Microsoft Windows, Linux, Android, ARM, AMD64, Intel, MacOS,
Abuses: IPFS System (majorly used in Blockchain File Hosting), Steam Game Platform
Suspected: Chinese TA
Methods: Arbitrary Powershell Command Execution, SSH Bruteforce, Network Scan
Also associated with : PrincessLocker Ransomware (myexternalip.com)
Track IPStorm
Clop Ransomware
The ransomware named “CLOP” is active in attacking organizations across the globe.
Recently the threat actors behind Clop have stolen and encrypted the sensitive information of various organizations. If there was a failure of ransom payment, the stolen information was leaked on their ‘CL0P^_- LEAKS’ data leak site, hosted on dark web. The leaked information includes data backups, financial records, thousands of emails and vouchers etc.
What does it do?
After encryption CLOP ransomware appends “.Clop” extension in each file and generates a text file “ClopReadMe.txt” containing ransom note in each folder. CLOP ransomware uses RSA (Rivest-Shamir-Adleman) encryption algorithm and generated keys are stored on a remote server controlled by Clop operators.
Newer versions of Clop have tried to expand their ransomware attack vectors through disabling and removing local security solutions such as Windows Defender and Microsoft Security Essentials etc. This ransomware can install additional password stealing Trojans and other malware attacks.
In most cases, Clop is distributed via fake software updates, trojans, cracks, unofficial software download sources, and spam emails. In a recent attack, it is suspected that the bug (CVE-2019-19781) in the Citrix Netscaler ADC VPN gateway was utilized to carry out the attack. Unfortunately, there’s no decryptor tool available for Clop ransomware.
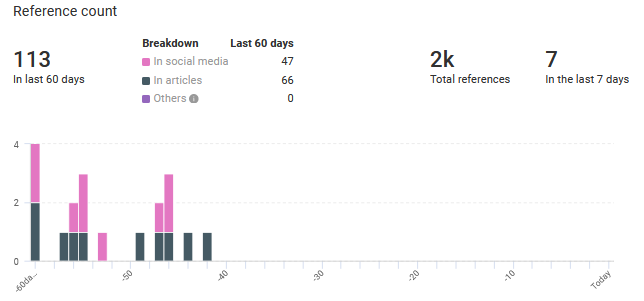
Malware threat intel from KNOW:
- 1,903 Reference(s) to this entity: First seen 11 Feb, 2019, last seen 15 Sep, 2020.
- Historic Sandbox Sighting – 2 sighting(s)
References:
Additional threat intelligence from our experts at the Netenrich Threat Research Center:
Business Model formed : since June 2020
Target: Windows
Victims: Software AG (German IoT Vendor), IndiaBulls (Finance) and many more
Threat Actor: FIN11 (deployed in their ops)
Methods: Process Injection, Fire Director Discovery, Proxy in C2C, Masquarade
Website: http://ekbgzchl6x2ias37.onion , https://outside-service.com
Track Clop Ransomware
Ryuk
Ryuk ransomware first appeared in August 2018. While not incredibly active across the globe, at least three organizations were hit with Ryuk infections over the first two months of its operations, landing the attackers about $640,000 in ransom for their efforts.
Ryuk itself possesses functionality that you would see in a few other modern ransomware families. This includes the ability to identify and encrypt network drives and resources, as well as delete shadow copies on the endpoint. By doing this, the attackers could disable the Windows System Restore option for users, and therefore make it impossible to recover from the attack without external backups.
What does it do?
The Ryuk ransom note is written to a file named RyukReadMe.txt. The body of the template remains the same, whereas the email ID and the Bitcoin (BTC) wallet address keep changing. It remains unclear if WIZARD SPIDER is copying the TTPs (tactics, techniques and procedures) and ransom notes of BitPaymer, or whether the groups may share information with each other.
Malware threat intel from KNOW:
- 20,706 Reference(s) to this entity: First seen 7 Mar, 2017, last seen 27 Oct, 2020
- Recent Sandbox Sighting – 25 sighting(s)
- Historic Sandbox Sighting – 279 sighting(s)
- Most recent reference: Any Run Sandbox result for ryuk.exe
- Related threat actors: FIN6, Wizard Spider, GRIM SPIDER, MixMaster, and Hidden Cobra.
- Industries targeted: Healthcare, Hospitals, Energy & Natural Resources, Education, Media & Entertainment, Information Technology, and Logistics.
- Related Intrusion Methods: Double Extortion, Phishing, Data Exfiltration, Spear Phishing, Data exfiltrate, Credential Stealing, Malware, etc.
- Hashes: 57
- Domains: 9
Additional threat intelligence from our experts at the Netenrich Threat Research Center:
Current State: Highly Active
Actors: FIN6, GRIM SPIDER, WIZARD SPIDER
Associated with: Hermes, BitPaymer
Collected Ransom: BTC Addresses
14hVKm7Ft2rxDBFTNkkRC3kGstMGp2A4hk :$64,477
1L9fYHJJxeLMD2yyhh1cMFU2EWF5ihgAmJ : 259,289.41 USD
15RLWdVnY5n1n7mTvU1zjg67wt86dhYqNj : 501,095.68 USD
1CN2iQbBikFK9jM34Nb3WLx5DCenQLnbXp : 96,086.55 USD
Latest Samples
MD5:
b8ebb6a557b474929505f647ebce05d6
a27c48e69f844508af66bb9e317d2c6f
ba59b52b445f45aaf8fb707445587b48
Track Ryuk
Get to KNOW
KNOW brings the power of advanced AI, intelligent filtering, and complex algorithms, all backed by expert insights to deliver rich, actionable context on breaking cyber news and threats. When something sparks your interest, log into KNOW for the who, where, why, and how.
Subscribe To Our Newsletter!
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.
Thank you for subscribing!