KNOW is Netenrich’s cybersecurity news aggregator and threat intel platform. You can see the most trending malware, threat actors, and vulnerabilities in our threat intel dashboard over the last 7 and 60 days. As per the dashboard, CVE-2020-29583 happens to be the most trending vulnerability in both these time frames.
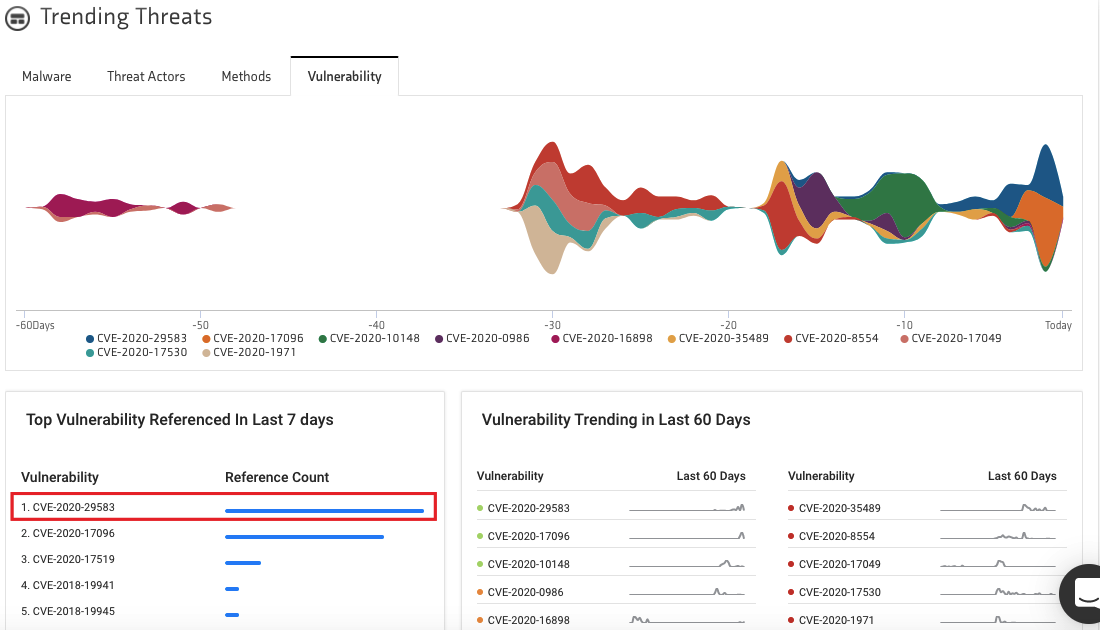
So, why is CVE-2020-29583 trending? Let’s take a look.
What is CVE-2020-29583?
Vendor: Zyxel
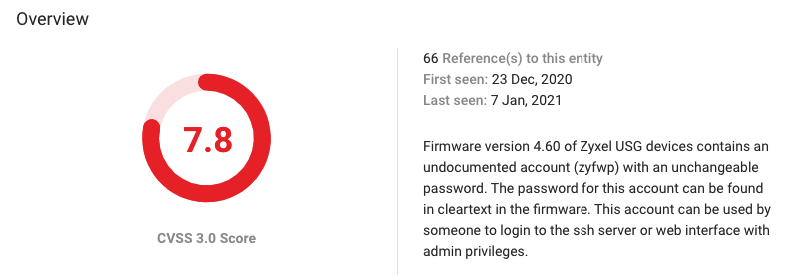
CVE-2020-29583 is a vulnerability in the firmware version 4.60 of Zyxel USG devices and contains an undocumented account (zyfwp) with an unchangeable password. The password for this account can be found in cleartext in the firmware. An attacker can use this account to login to the ssh server or web interface with admin privileges.
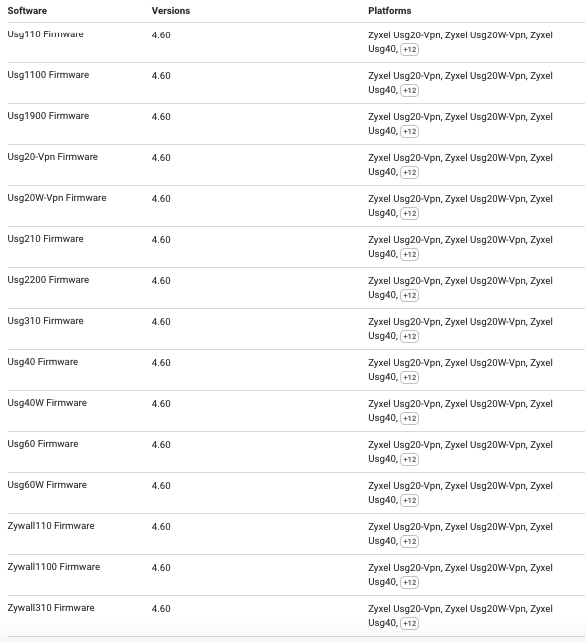
Here is a tabulation of all the software that are currently vulnerable.
Patch
- http://ftp.zyxel.com/USG40/firmware/USG40_4.60(AALA.1)C0_2.pdf
- https://businessforum.zyxel.com/discussion/5252/zld-v4-60-revoke-and-wk48-firmware-release
- https://businessforum.zyxel.com/discussion/5254/whats-new-for-zld4-60-patch-1-available-on-dec-15
- https://www.zyxel.com/support/CVE-2020-29583.shtml
- https://www.zyxel.com/support/security_advisories.shtml
- A fix for the NXC access point controller series products would not be released until April.
Why is CVE-2020-29583 trending?
Earlier this week, the Multi-State Information Sharing and Analysis Center, or MS-ISAC, issued an alert that the CVE-2020-29583 vulnerability poses a major cybersecurity risk for large enterprises and government agencies. According to the researchers, around 100,000 Zyxel devices are vulnerable to the backdoor.
As per MS-ISAC:
This could allow the attacker to change firewall settings, intercept traffic and create VPN accounts to gain access to the network behind the device and other administrative functions.
While no exploits have been spotted in the wild, the MS-ISAC notes that a threat actor could leverage this vulnerability to gain admin access to their targeted network’s inner parts and escalate privileges.
Reactions from Twitter
#1 Security Bulletin
Hard-coded admin-level backdoor found in more than 100k Zyxel network devices https://t.co/TFWQ2nvs5P pic.twitter.com/idfrmpLfxL
— Virus Bulletin (@virusbtn) January 4, 2021
#2 The Hacker News
WARNING: A Secret Hard-Coded Backdoor Account Found in Some Zyxel Firewall, VPN Products
Read details: https://t.co/gD1vNC7nRy#infosec #cybersecurity
— The Hacker News (@TheHackersNews) January 1, 2021
#3 Techmeme
Researchers: more than 100K Zyxel firewalls and VPN gateways have a hardcoded admin-level backdoor that can grant attackers root access to devices (@campuscodi / ZDNet)https://t.co/8Lrl7SGW22https://t.co/WdbHLfoqnA
— Techmeme (@Techmeme) January 2, 2021
CVE-2020-29583 references from KNOW
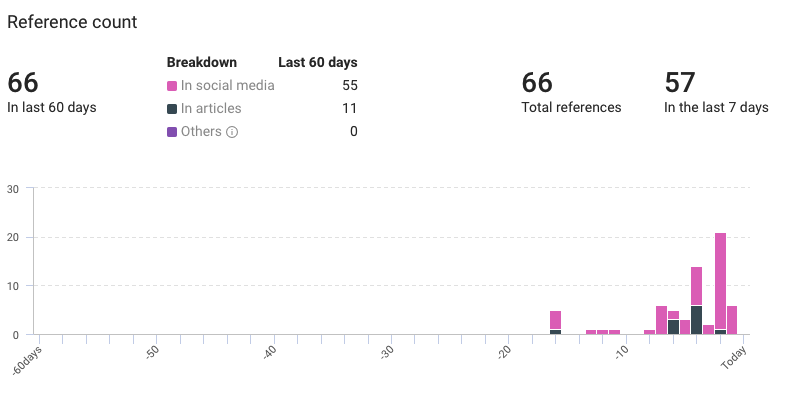
- First seen: 23 December 2020
- Last seen: 7 January 2021
- Total references: 66
- Last 60 days: 66
- Previous 7 days: 57
KNOW our powerful threat intelligence platform
KNOW is Netenrich’s Threat Intel Platform that extracts data from billions of data points and correlates relevant intel and expert analyst insights to help you follow, search, and act—in a fraction of the time it takes now. However, Netenrich’s offering isn’t just limited to threat intelligence. We offer a powerful combination of threat and attack surface intelligence.
Threat and Attack Surface Intelligence will help your SecOps to:
- Find hidden risks to your brand on the public Internet
- Stay informed about threats in minutes versus hours
- Act on the most critical threats first
- Reduce effort and alert fatigue
- Measure and demonstrate value.
Find out more about Netenrich’s Attack Surface Intelligence (ASI) solution.
Hey, before you leave, we have this interesting article up on “Intelligent SOC.” Intelligent SOC leverages Netenrich Resolution Intelligence to evolve cybersecurity beyond the antiquated ticket-based model with modern AIOps-based architecture.
Want to read some more?
Yes I do!
Subscribe To Our Newsletter!
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.
Thank you for subscribing!