As detected by KNOW’s threat intel dashboard, APT1 Comment Crew was by far the most referenced threat actor of the last seven days.
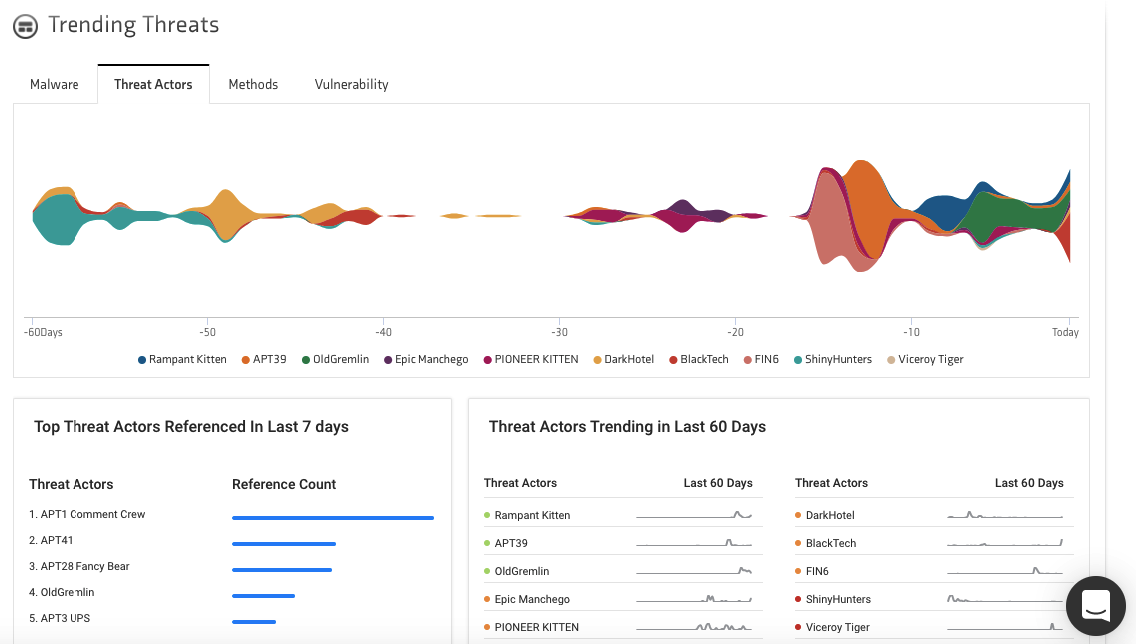
Who are the APT1?
APT1 is a Chinese threat group that has been attributed to the 2nd Bureau of the People’s Liberation Army (PLA) General Staff Department’s (GSD) 3rd Department, commonly known by its Military Unit Cover Designator (MUCD) as Unit 61398.
Aliases: Byzantine Candor, APT1, PLA Unit 61398, Comment Group, TG-8223, Comment Panda, and Group 3.
APT1 has stolen hundreds of terabytes of data from 141 organizations and has the capability to steal data from dozens of organizations simultaneously.
Who does the APT1 Target?
The group has targeted international cooperation and development agencies, foreign governments in which English is one of the multiple official languages, and multinational conglomerates that primarily conduct their business in English. Their victims are located in the US, Canada, and the UK.
The industries targeted by them, as detected by KNOW are:
- Finance
- Aerospace and defense
- Manufacturing
- Media and entertainment
- Healthcare
- Telecommunications
- Education
- Energy and natural resources
- Engineering
- Transportation
- Electronics
- Information technology
- Research
- Food and beverage
- Chemicals
- Agriculture
- Construction
The Infamous APT1
APT1 or PLA Unit 61398 was officially indicted on 19 May 2014 by the US Department of Justice. Five members of the group were indicted on charges of theft of confidential business information and intellectual property from U.S. commercial firms and for planting malware on various systems. Forensic evidence traced APT1’s base of operations to a 12-story building off Datong Road in a public, mixed-use area of Pudong in Shanghai.
References counted by KNOW
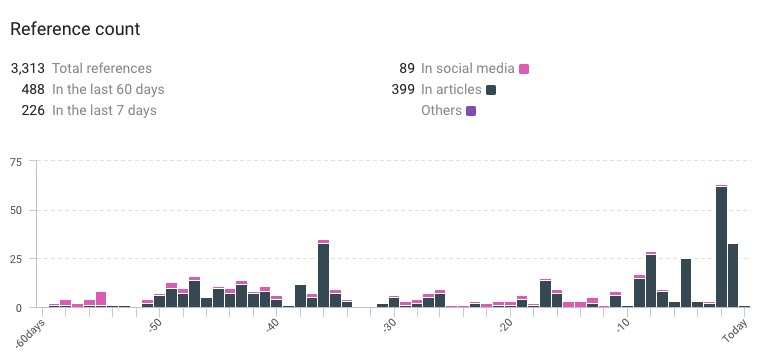
- Total references: 3,313
- References in the last 60 days: 488
- References in the last 7 days: 226
Context taken from KNOW
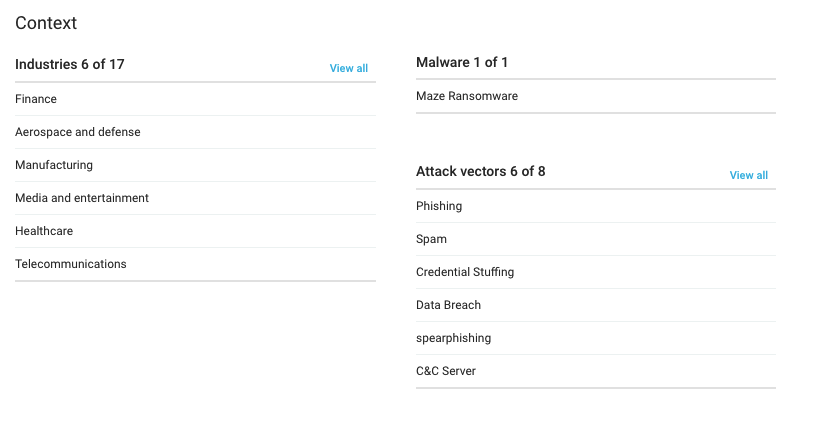
- Risk rules triggered: 5 out of 48
- Most recent sandbox sighting: Any Run Sandbox result for DAT 20200924 OQI0784.malware
- Related Intrusion Methods: Phishing, Spam, Credential Stuffing, Data Breach, Spear Phishing, and Social Engineering.
- Malware: Maze Ransomware.
Thoughts from the Twitter-verse
Good evening everyone.
I’m glad so many of you found the FBI and Europol cards entertaining. Smiling face with halo
We started assembling our APT/Nation State archive. We have begun with APT1 (Comment Crew, Unit 61398).
https://vxug.fakedoma.in/archive.html
We have a lot of work to do. Have a nice night.
Yanbian Gang, KovCoreG, APT1 Comment Crew (Unit 61398), APT23 (KeyBoy,PiratePanda), APT32 OceanLotus attack groups that have been active for the past week. We’ve detected about 15 new malware.
Win32.Neshta.A
Win32.Expiro.Gen
W32/Bloat-A
W32/HLLP.41472.e
#CyberSecurity
Using Threat Intelligence and SOC-as-a-Service
KNOW is Netenrich’s Threat Intel Platform that extracts data from billions of data points and correlates relevant intel and expert analyst insights to help you follow, search, and act—in a fraction of the time it takes now. If you want to know more about KNOW then read this. KNOW can be a life-saver for your SOC team.
However, what if you don’t have a SOC team?
Maintaining a dynamic SOC team is hard, and your security team already handles a wide variety of tasks that leaves little time for business-critical needs. Keeping a SOC running efficiently 24/7 stands to grow even more challenging for the foreseeable future. This is where Netenrich’s SOC-as-a-Service can be immensely helpful.
We bring extensive resources and expertise across threat hunting, log analysis, and other activities to complement your existing operations. Our team of 80+ analysts and admins have decades of experience working across vertical industries and can efficiently onboard and scale services.
Want to know more? Then read this.
Subscribe To Our Newsletter!
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.
Thank you for subscribing!




